



- •
- themarkup.org
- •
- 1Y
- •
Email alias indeed helps to avoid spam and helps you to assume separate identity per site, but won’t help in any way to stop mail provider/server from processing your email data for user profiling / targeted ad purpose.
Buying email domain and self-hosting is only the full proof way from privacy POV, but it is really difficult target to accomplish. A privacy respecting email hosting + alias should be next ideal choice, IMO.


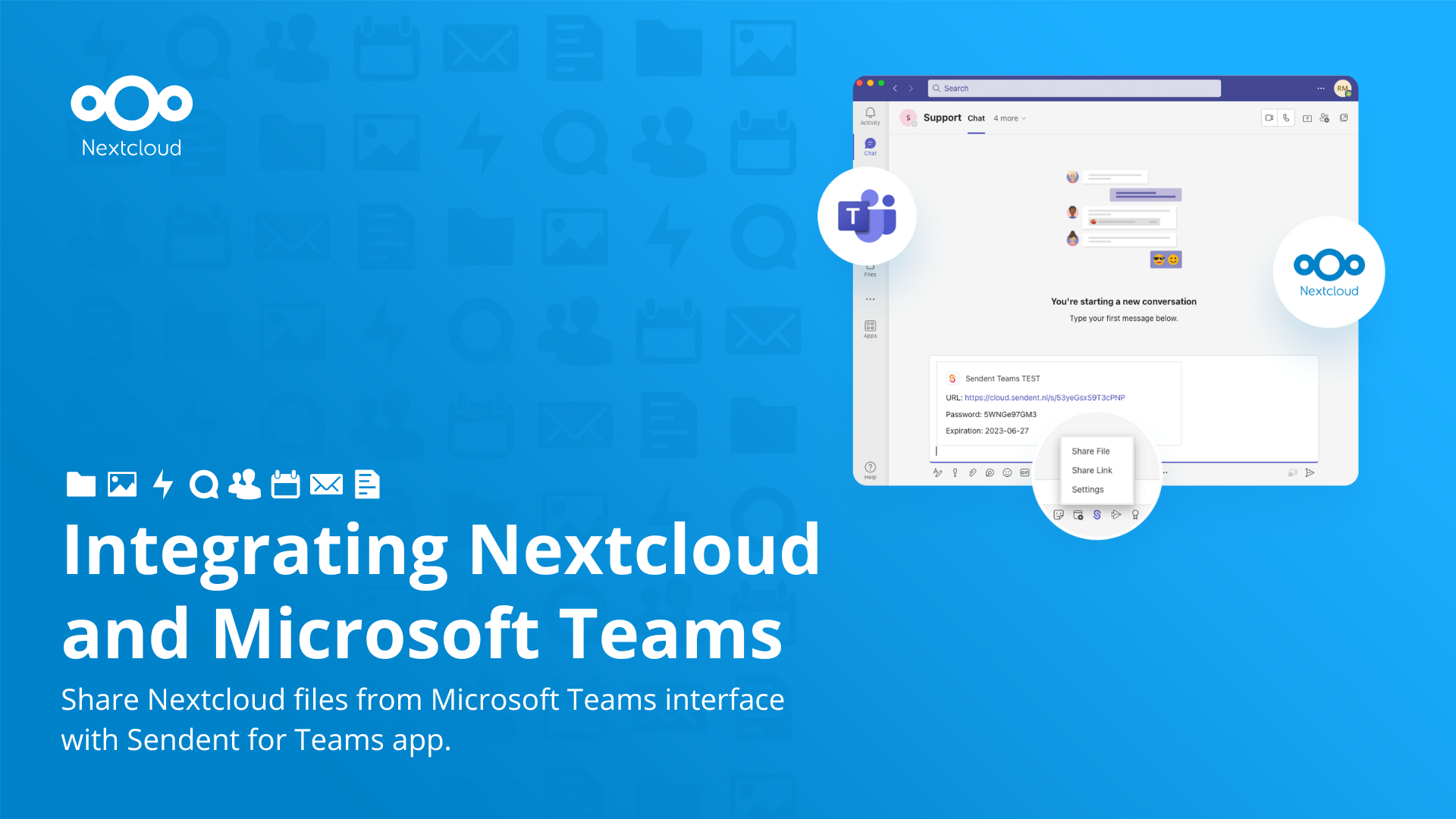
The post is about Nextcloud self-hosted file storage as an open source replacement for One Drive which is deeply integrated with MS Teams. For those, who can’t replace MS Teams with FOSS equivalent for whatever reason, can at least stop relying on One Drive for file storage solution.
And, for your information, Nextcloud does offer 1:1 and group chat solution[1], which is an open source replacement for MS Teams.


Nextcloud[1] is an open source and self-hostable SaaS product.
Instead of using OneDrive and Google Drive (and similar proprietary solutions), Nextcloud is a better solution from Privacy POV, IMO.


- •
- nextcloud.com
- •
- 2Y
- •
And, here come typical response -
telecom operators have informally shared with the department that the leaked information claimed in the ClouSEK report seems to be a compilation of old data sets of telecom subscribers and it is not due to any vulnerability in their system."


- •
- www.ghacks.net
- •
- 2Y
- •


- •
- themarkup.org
- •
- 2Y
- •


- •
- www.wired.com
- •
- 2Y
- •
Request: Your IP > Apple (1st) relay node > 3rd party (2nd) relay node > Website
Response: Your IP < Apple (1st) relay node < 3rd party (2nd) relay node < Website
Whoever has access to both relay nodes, can easily track you end-to-end.
As for Apple, they claim the 1st relay node is owned by them, and 2nd relay node is owned by 3rd party. (Source: https://www.apple.com/icloud/docs/iCloud_Private_Relay_Overview_Dec2021.pdf)
In theory, it should not be a privacy concern because -
- Website will see the request coming from 2nd relay node’s IP.
- 2nd relay node will see the request is coming from Apple (1st) relay node’s IP.
- So, only Apple knows your IP.


The really powerful thing about Facebook ads is in your ability to layer targeting options on top of one another, gradually making your audience more and more specific. An extreme (and hilarious) example of the power of hypertargeting was featured in AdWeek last year, when a marketing pro targeted his roommate with ads so specific the poor guy thought he was being cyberstalked.
🤮
I’m afraid that protection might not last long.


sold ad analytics
Do you still the have the link to news article where it was reported?
Earlier I was using Pi-Hole on my network then switched to AdGuard Home (not same as AdGuard DNS) as it is an open source product with in-built DOH support (yes, I can setup Pi-Hole to do the same, but that’s an extra manual configuration) and Privacy Guide seems to recommend it over Pi-hole. After reading your post, I tried to lookup more about it. Nothing on Wiki. Closest thing is this. If the allegations are true then I need to switch back to Pi-Hole.
If installing extension is not an option for you -
- You can open https://snowflake.torproject.org/ (or https://relay.love/) on a tab,
- scroll down to ‘Leave this browser tab open or embed a web badge on your website’ section
- toggle ‘Enabled’ button
- and leave the browser running.
- Note: Browser needs to have WebRTC enabled to make it work.
I’m personally running Snowflake container on docker on my little Raspberry pi 24/7. And, yes, in 2023 most of the connection to my bridge was from Iran.


- •
- www.ghacks.net
- •
- 2Y
- •


- •
- www.ghacks.net
- •
- 2Y
- •


It’s a sell and not leak of data. It’s actually called Server to Server (S2S) tracking.
https://tinuiti.com/blog/data-privacy/server-to-server-tracking/


This is how I explained it to one of my friends who is/was definitely a member of “I’ve got nothing to hide” club -
- Suppose you are in a pay-to-use toilet minding your own Business.
- That pay-to-use toilet is managed by a public/private entity called ToiletBook.
- Suddenly you notice a (hidden) camera in the room.
- When confronted, the owner confirms the only reason they took your picture to suggest you the perfect underwear based on your size. And, there is a legal guarantee that picture/data will never be used for any other purpose and only be processed by machine.
- Will you still go to such toilet?
BTW, that friend stopped talking to me afterward; not sure why 🤔 (Edit: I should stop giving shitty examples to anyone, as it seems ) 🤐


Back in '50s, the connection between Tobacco products and Cancer was evident. Since '70s connection between Fossil fuel and Global warming was evident.
Yet, no one heeded those warnings at the time. With cancer rate going up, and climate becoming increasing unpredictable/extreme, people now started to take notice.
With so much information to process, Human brain ignores information that doesn’t have a clear relation to a significant real world problem that immediately impacts their lives. This makes us intelligent (at short term) and dumb (at long term) at the same time.
Using a service at free of cost (at the expense of your privacy) is acceptable by majority of population as it has no significant real world impact on their lives.
If tomorrow, a huge data leak from these imbecile data hoarders leads to massive transaction fraud/identify theft that impacts a significant percentage of population and their daily lives, only then there will be massive outrage that you expect.
Till then, we are the only one who escaped the Matrix, while rest embraced it.


- •
- themarkup.org
- •
- 2Y
- •


- •
- themarkup.org
- •
- 2Y
- •


- •
- www.wired.com
- •
- 2Y
- •


Lemmy website does provide official PWA app.
On iOS: Safari > Lemmy website > Hit share button > Add to home screen. On android, I assume steps will be similar.
I wholeheartedly recommend PWA app as such is published by the publisher of website itself, and I don’t need to download it either from official or 3rd party store.
In case you don’t know, PWA is basically a web app, running using your browser engine, which has almost same look-n-feel of native app.


- •
- 9to5mac.com
- •
- 2Y
- •


- •
- themarkup.org
- •
- 2Y
- •


I personally use Invidious (Privacy front-end of YouTube) using Docker. Though it can be compiled and run standalone as well.
It doesn’t take much resource (< 100 MB) to run on my system. There is NO ad or no pause.
It’s like YouTube Premium account with ZERO tracking.
https://addons.mozilla.org/en-US/firefox/addon/i-dont-care-about-cookies/
One of those extensions recommended by Mozilla.


To add more context to it -
Meta is actually trying to comply circumvent EU’s strict privacy policy.
Recently, The EU’s top court said in July that Meta must first get consent before showing ads to users - a ruling that jeopardises the company’s ability to make money by tailoring advertisements for individual users based on their online interests and digital activity.
I personally consider this[1] to be the ultimate test of Browser fingerprint protection coverage. Let me know if you manage to find a way to defeat this test.
This is another good website for Browser leak/privacy settings test.


















Ah! I was not aware of the fact that Alias service can encrypt email before forwarding to actual mailbox.