- AnimalsDream
- •
- lemmy.ml
- •
- 2d
- •
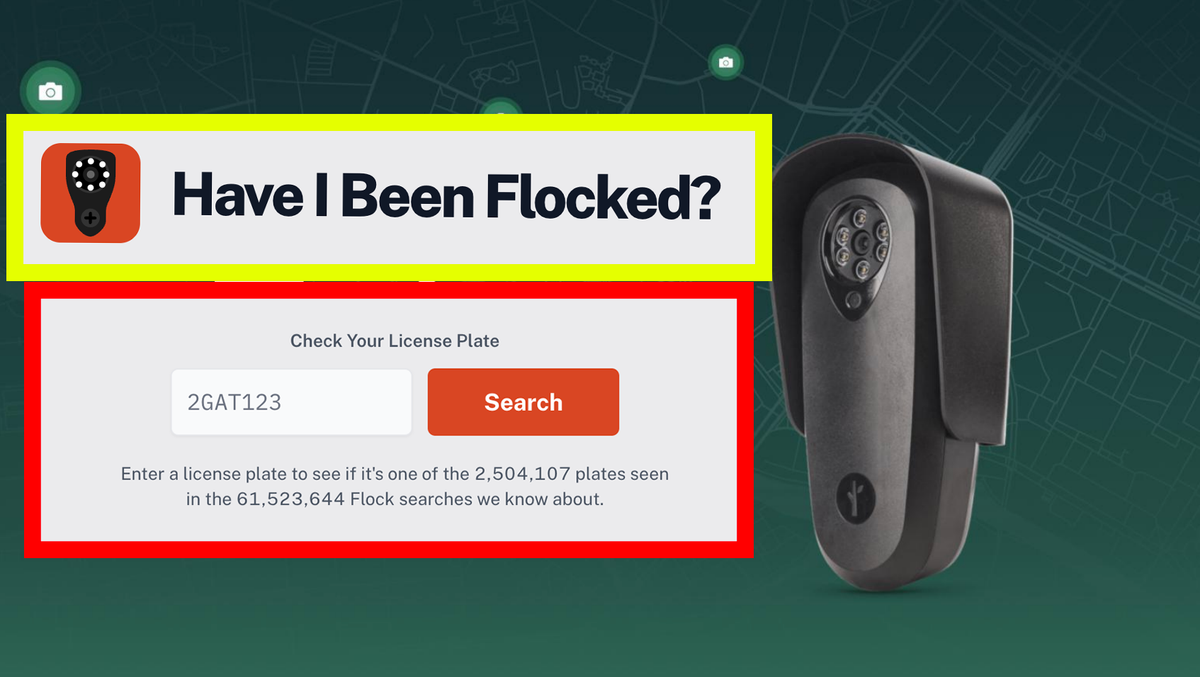
For context, in my password manager I had tried formatting some of my entrees so that it would contain the usual username and password, but instead of creating whole new entrees for the security questions for the same account, I just added additional fields in the same entree in order to keep things a little more tidy.
I was not expecting that doing so would result in later being shaken down by Proton to pay even more money just to access the same few bytes of fucking text I had trusted them with. This is sleazy as fuck and I am dropping these idiots entirely.
Hello!
As a handsome local AI enjoyer™ you’ve probably noticed one of the big flaws with LLMs:
It lies. Confidently. *ALL THE TIME.*
(Technically, it “bullshits” - https://link.springer.com/article/10.1007/s10676-024-09775-5
I’m autistic and extremely allergic to vibes-based tooling, so … I built a thing. Maybe it’s useful to you too.
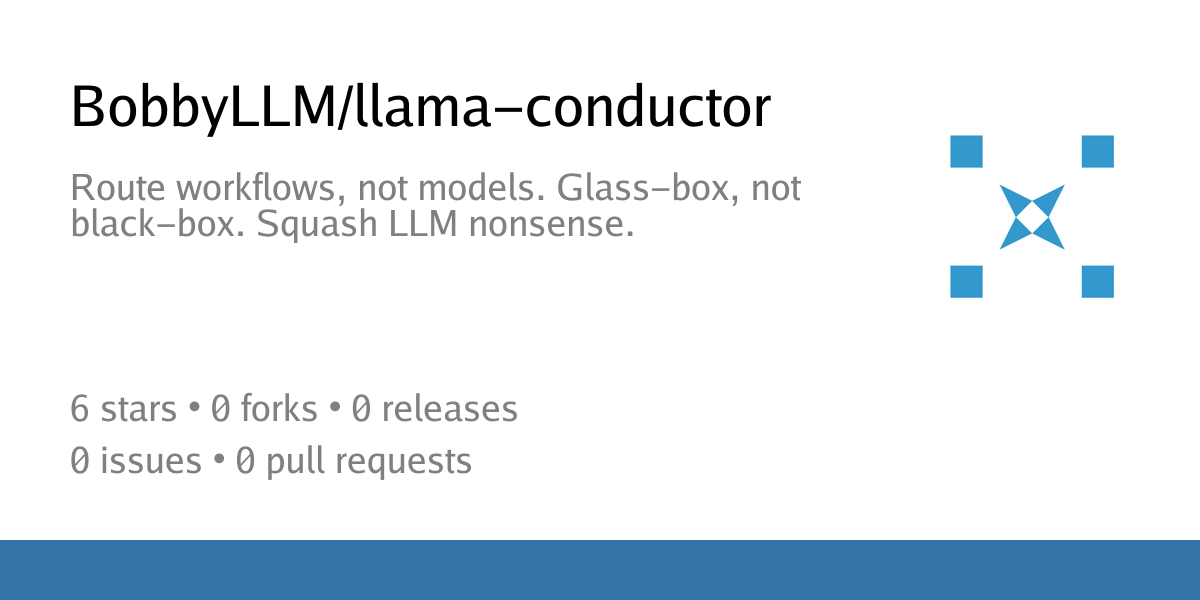
## The thing: llama-conductor
**llama-conductor** is a router that sits between your **frontend** (OWUI / SillyTavern / LibreChat / etc) and your **backend** (llama.cpp + llama-swap, or any OpenAI-compatible endpoint). Local-first (because fuck big AI), but it should talk to anything OpenAI-compatible if you point it there (note: experimental so YMMV).
Not a model, not a UI, not magic voodoo.
A glass-box that makes the stack behave like a **deterministic system**, instead of a drunk telling a story about the fish that got away.
TL;DR: *“In God we trust. All others must bring data.”*
Three examples:
## 1) KB mechanics that don’t suck (1990s engineering: markdown, JSON, checksums)
You keep “knowledge” as dumb folders on disk. Drop docs (`.txt`, `.md`, `.pdf`) in them. Then:
* `>>attach <kb>` — attaches a KB folder
* `>>summ new` — generates `SUMM_*.md` files with **SHA-256 provenance** baked in
* `>> moves the original to a sub-folder
Now, when you ask something like:
> “yo, what did the Commodore C64 retail for in 1982?”
…it answers from the attached KBs *only*. If the fact isn’t there, it tells you - explicitly - instead of winging it. Eg:
> The provided facts state the Commodore 64 launched at $595 and was reduced to $250, but do not specify a 1982 retail price. The Amiga’s pricing and timeline are also not detailed in the given facts.
>
> Missing information includes the exact 1982 retail price for Commodore’s product line and which specific model(s) were sold then. The answer assumes the C64 is the intended product but cannot confirm this from the facts.
>
> Confidence: medium | Source: Mixed
No vibes. No “well *probably*…”. Just: here’s what’s in your docs, here’s what’s missing, don't GIGO yourself into stupid.
And when you’re happy with your summaries, you can:
* `>>move to vault` — promote those SUMMs into Qdrant for the heavy mode.
## 2) Mentats: proof-or-refusal mode (Vault-only)
**Mentats** is the “deep think” pipeline against your **curated** sources. It’s enforced isolation:
* no chat history
* no filesystem KBs
* no Vodka
* **Vault-only grounding** (Qdrant)
It runs triple-pass (thinker → critic → thinker). It’s slow on purpose. You can audit it. And if the Vault has nothing relevant? It refuses and tells you to go pound sand:
```
FINAL_ANSWER:
The provided facts do not contain information about the Acorn computer or its 1995 sale price.
Sources: Vault
FACTS_USED: NONE
[ZARDOZ HATH SPOKEN]
```
Also yes, it writes a mentats_debug.log, because of course it does. Go look at it any time you want.
The flow is basically: **Attach KBs → SUMM → Move to Vault → Mentats**. No mystery meat. No “trust me bro, embeddings.”
## 3) Vodka: deterministic memory on a potato budget
Local LLMs have two classic problems: goldfish memory + context bloat that murders your VRAM.
**Vodka** fixes both without extra model compute. (Yes, I used the power of JSON files to hack the planet instead of buying more VRAM from NVIDIA).
* `!!` stores facts verbatim (JSON on disk)
* `??` recalls them verbatim (TTL + touch limits so memory doesn’t become landfill)
* **CTC (Cut The Crap)** hard-caps context (last N messages + char cap) so you don’t get VRAM spikes after 400 messages
So instead of:
> “Remember my server is 203.0.113.42” → “Got it!” → [100 msgs later] → “127.0.0.1 🥰”
you get:
> `!! my server is 203.0.113.42`
> `?? server ip` → **203.0.113.42** (with TTL/touch metadata)
And because context stays bounded: stable KV cache, stable speed, your potato PC stops crying.
---
There’s more (a lot more) in the README, but I’ve already over-autism’ed this post.
TL;DR:
If you want your local LLM to **shut up when it doesn’t know** and **show receipts when it does**, come poke it:
* **Primary (Codeberg):** https://codeberg.org/BobbyLLM/llama-conductor
* **Mirror (GitHub):** https://github.com/BobbyLLM/llama-conductor
PS: Sorry about the AI slop image. I can't draw for shit.
PPS: A human with ASD wrote this using Notepad++. If it the formatting is weird, now you know why.

- •
- 10h
- •
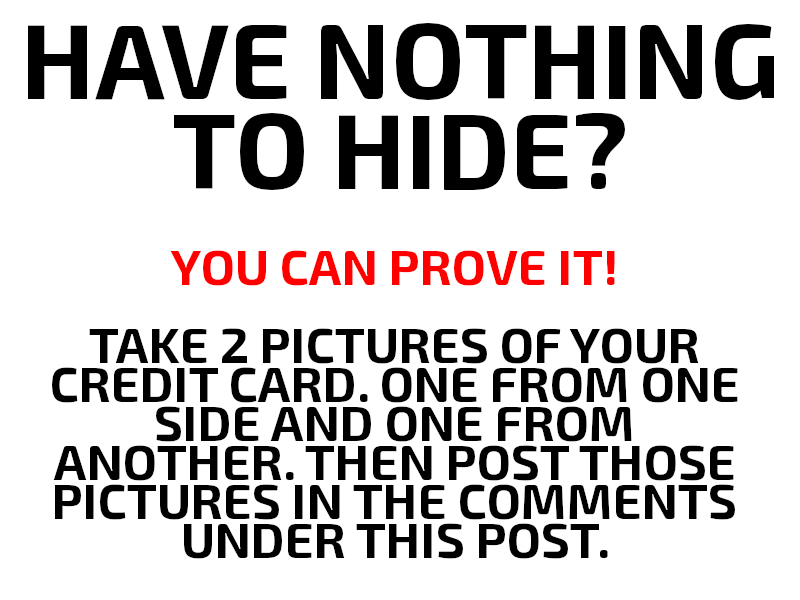
So I just posted a picture of a satirical "You have nothing to hide?" and it was deleted. Can I find out why I was removed? It's a satire of the "Well I have NOTHING to hide so why should I care about data collection" argument and how that's turned into showing IDs and Credit Cards. Someone I know said that they created it two days ago and just wanted to share it for others to share so that we can address this ludicrous mindset.
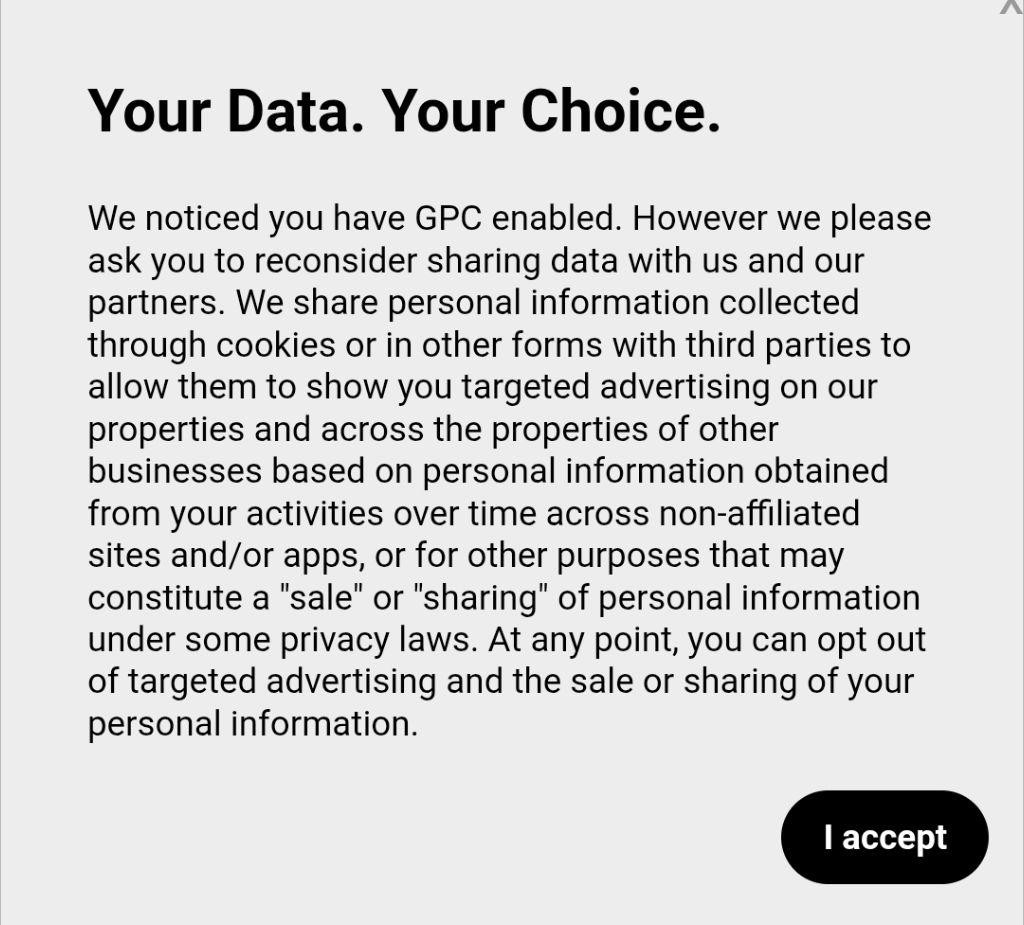
So browsers have started to roll out GPC, or basically browser-based consent. This was explicitly designed to deal with intrusive cookie banners. I've now noticed several websites with the same intrusive banners recognizing that you opted out but begging you to opt back in anyway. These banners are so big as to obscure the majority of the content on the site.
cross-posted from : https://lemmy.zip/post/57521167
> Over the past years, repeated investigations have shown that at least 14 EU Member States have deployed spyware against journalists, human rights defenders, lawyers, activists, political opponents, and others.
> Despite the findings of the European Parliament’s PEGA Inquiry Committee in 2023, and the push from human rights organisations, the European Commission has so far refused to propose binding legislation to prohibit spyware. Not only that: it has done nothing. Right now, no EU-wide red lines exist against the use of spyware. This means that victims lack effective remedies, authorities face no scrutiny, and commercial spyware vendors continue to operate with near-total impunity, enriching themselves by violating human rights, and even benefiting from European public funding.
Translated from German (with DeepL):
> The Swiss messenger service Threema is being acquired by the German investment company Comitis Capital. Both the company and Threema itself emphasize that the arrival of the new investor will not lead to any significant changes for the time being. The company headquarters and servers will remain in Switzerland, and the management team will stay unchanged.
>
> # A financial investor with a broad portfolio
>
> Comitis Capital is a young private equity firm, not a technology company. It invests in various industries, including a UK-based supplier of vegan meat alternatives and a manufacturer of dog accessories.
>
> Its business model consists of providing financial support to promising companies so that they can grow and establish themselves internationally. “Comitis now clearly sees this potential in Threema too,” says SRF digital editor Tanja Eder.
>
> # Data protection as a business model
>
> The strong focus on data protection is considered a key strength of the messenger. Precisely because US tech companies are coming under increasing criticism and digital sovereignty is gaining in importance, Comitis sees this aspect as a clear unique selling point.
>
> Whether this will remain the case in the long term is unclear, according to Eder. If Comitis were to conclude at some point that it would be more profitable to collect Threema customer data or sell the company, no one could prevent them from doing so.
>
> # Trust in the authorities remains an issue
>
> In Switzerland, federal authorities and the military also use Threema for internal communication. Even though everyone involved is aware that there is no such thing as absolute security, Threema still has advantages over its competitors.
>
> For example, Threema's source code is openly accessible. Experts in the fields of data protection, IT security, and research regularly check whether the company is keeping its promises. Government agencies can also carry out their own checks.
>
> # Hardly any alternatives on the market
>
> Good alternatives to Threema are rare. “Apart from WhatsApp, which dominates the market, there is simply not much room for other messenger services,” notes the digital editor.
>
> Signal is considered another secure messenger alongside Threema. However, it is operated from the US, albeit by a non-profit foundation and financed by donations. In Switzerland, Proton offers encrypted emails, but does not have its own messenger service.
>
> “Given this limited offering, we can only hope that privacy-friendly communication services will gain in importance in the future,” says Eder.
I only want to use it for facebook marketplace, but jeez i didnt know they were taking it this far with this crap...
Can Android apps use WebRTC, or is WebRTC only available in browsers?
If Android apps can use WebRTC, how can it be blocked per app or system-wide to prevent IP or network leaks?
cross-posted from: https://lemdro.id/post/35049920
>The latest update for the popular Nova Launcher app includes Facebook Ads and Google AdMob.
>
> Compare 8.2.4: https://reports.exodus-privacy.eu.org/en/reports/698198/
>
> With 8.1.6: https://reports.exodus-privacy.eu.org/en/reports/673643/
>
> From 2 trackers to 6 trackers. From 30 permissions to 36. And two of the "trackers" are for ad stuff, like Facebook Ads.
>
> I believe the owner also changed. It's no longer Branch, but something called Instabridge Sweden.
I want to leave my phone at home or not have it on me most of the time. Most calls I get are meaningless spam and I rarely need to answer my phone for real calls outside my home (though it does happen on ocassion). One thing I do want and am accustomed to is having music, however.
I was looking at Amazon and Aliexpress for devices that can play mp3/mp4s, some can do that and even have ebook readers which is great. I don't see any connectivity on them or microphones save for the one that is included on the earbuds or Bluetooth.
And that is one question I have: can Bluetooth compromised your privacy? I know Bluetooth hacking is real but how bad is it?
I guess if it has a microphone it is ok if I dont have any connectivity. What do you guys recommend?
For some of them I kind of lost access so I would need to write emails to instagram or whatever, for others I would need to remember and to access to each one of them and delete them.
The hardest would be gmail with people having my contacts from like 10 years ago..
We have no marketing budget and are trying to get as many people away from Big Tech surveillance as possible. Please share this link with friends and family, and on social media.
It contains a full link index of all our Alternatives pages, as well as links to our Big Tech Walkout programme, and a Quick Start section for those who just want to grab the top choices.
Thank you!
Patrick (Rebel Tech Alliance)
TL;DR
ID scanning is becoming a more common requirement to access bars and clubs in Australia (and worldwide). A company called ScanTek is used in over 1,000 clubs in Aus and provides tools such as biometric-matching someone's face to an ID, detecting fake IDs, flagging people and sharing data with other venues automatically
As well as verifying ages, ScanTek boasts *"collect marketing information from IDs and drivers licences, which business owners can use to target specific demographics with promotions"* on its website in a pitch to business owners. Though they claim to not share any of this with third parties
Australia's privacy laws are vague, don't specify what can be collected and how it must be stored, and only say that companies shouldn't keep data for longer than is "reasonable"
- @tdTrX@lemmy.ml
- •
- 5d
- •
# Data can be transferred using ultrasonic frequencies,
# Legit Uses -
Google Tone
Google Tez
# Bad Thing -
It has been used in the past for malicious activity by governments (if you know, you know).
I can be used to track people, like people's devices screaming their ID and devices receiving other devices IDs.
Imagine a mall with ultrasonic beacons, and for iOS and Google Play Services, hear that.
# Reports -
https://techcrunch.com/2018/01/02/some-apps-were-listening-to-you-through-the-smartphones-mic-says-report/
https://thehackernews.com/2017/05/ultrasonic-tracking-signals-apps.html
https://www.youtube.com/watch?v=1n_8zDIFmQU
# Solution ?
How to stop my devices like browsers, Windows PC, macOS, Android, and Android apps, from sending and receiving these frequencies
THis is a dead Chrome extension - https://github.com/ubeacsec/Silverdog
cross-posted from: https://hexbear.net/post/7371980
> cross-posted from: https://news.abolish.capital/post/20716
>
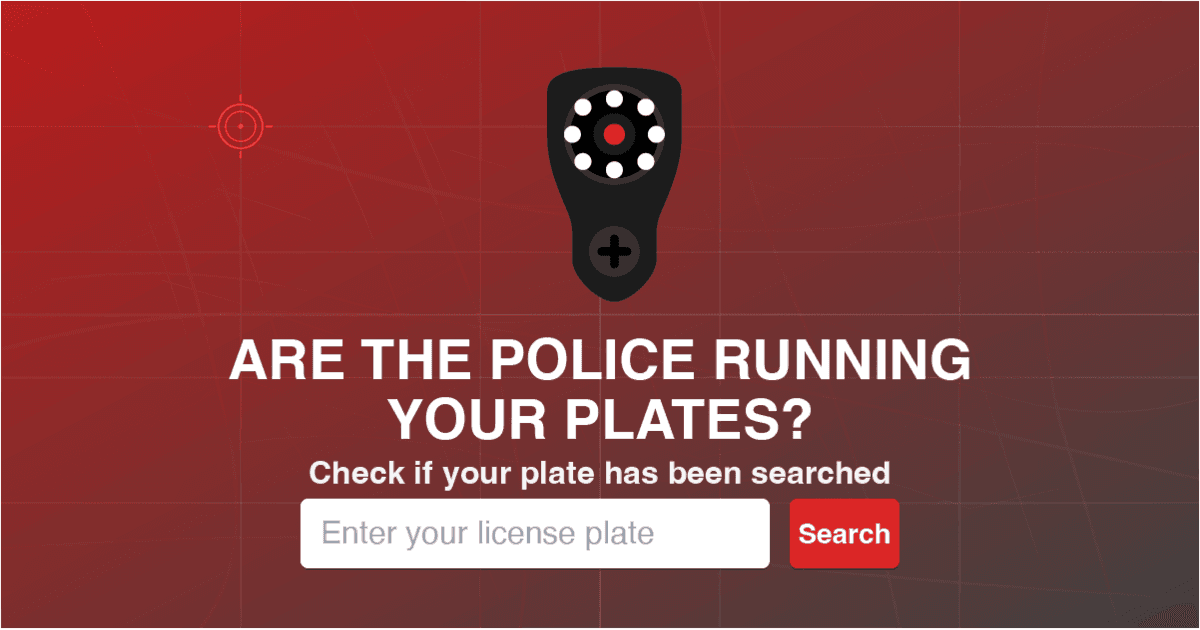
> > While New York City, Los Angeles, and Chicago have all received significant attention when it comes to police use of surveillance technologies, the small city of New Orleans has for years been the laboratory for a sophisticated surveillance apparatus deployed by the city’s police department and other policing bodies.
>
> >Just last year, New Orleans was in the news as the city considered setting a new surveillance precedent in the United States. First, a privately run camera network, Project N.O.L.A., was exposed for deploying facial recognition technology, including “live use” (meaning Project N.O.L.A. was identifying people in real time as they walked through the city). All of this was done in close collaboration with the local police, despite these uses violating a 2022 ordinance that placed narrow limits on the use of facial recognition.
>
> >Then the city flirted with formally approving the use of live facial recognition technology, which would have been a first in the United States. If enacted, live facial recognition technology would allow police to identify individuals as they move about New Orleans in real time. All of this occurred in the months before the Trump administration deployed Border Patrol and Immigration and Customs Enforcement (ICE) agents, wielding an array of surveillance technologies, to terrorize and kidnap New Orleans residents. Of course, New Orleans residents have organized and actively fought back against the police and their spying, offering lessons for organizers across the country.
>
> >Edith Romero, an organizer with Eye on Surveillance (EOS), spoke with Truthout about the history of Eye on Surveillance, Project NOLA, the use of facial recognition technology in New Orleans and why we should all be watching what’s happening there if we’re concerned about the growing surveillance state.
> >
> > [Source](https://truthout.org/articles/battle-over-facial-recognition-in-new-orleans-will-shape-future-of-surveillance/)
> >
> > ---
> >
> > **From [Truthout](https://truthout.org/feed/?withoutcomments=1) via [This RSS Feed](https://truthout.org/feed/?withoutcomments=1).**
What do you think of the Nora Android app and desktop browser optimized for social networking services? Does anyone use it? Is it safe and private?
Github link: https://github.com/nonbili/Nora
F-droid link: https://f-droid.org/packages/jp.nonbili.nora
- @tdTrX@lemmy.ml
- •
- 8d
- •
https://play.google.com/store/apps/details?id=com.mmi.maps
- @tdTrX@lemmy.ml
- •
- 7d
- •
There are many formats for blocklists for Domain, Subdomain, URL, Filterlist
Like uBlock, Adblock, AdGuard
Which are compatible with which
What are the pros and cons of each

- •
- 9d
- •
So I was reading [this article](https://arstechnica.com/security/2026/01/signal-creator-moxie-marlinspike-wants-to-do-for-ai-what-he-did-for-messaging/) about Signal-creator Moxie Marlinspike's new project, [Confer](https://confer.to/) , which claims to be a verifiably E2E encrypted LLM chat service. There are a couple of short [blog articles](https://confer.to/blog/2026/01/private-inference/) that give the gist of it, and some github repos including [this one](https://github.com/conferlabs/confer-image) that includes scripts for producing the VM that will run your particular LLM session. But if I'm following this all correctly, it implies that every chat session (or perhaps every logged-in user) would have their own VM running their own LLM to ensure that the chain of trust is complete. This seems impossible from a scalability perspective, as even small LLMs require huge quantities of RAM and compute. Did I miss something fundamental here?
**Built With AI** *to make a safe space out of its reach!*
[Demo Video](https://streamable.com/qajqvc)
[Source](https://gitlab.com/here_forawhile/spreadsheet)
This privacy tool can be installed on most Linux distros, including my favorite....hosting from termux (android)!
The project was driven by a my desire to create a private space for spreadsheet collaboration with no fluff, tracking ect.
Fully open and free tech stack
- SQLite Database
- Gunicorn WSGI Server backend
- Python for API and Application Routes
- Pure JS, HTML, CSS Frontend
- TOR for worldwide encrypted connection to the service.
Formulas
Supported functions include:
- Math: SUM, AVERAGE, MIN, MAX, COUNT, ABS, - ROUND, SQRT, POWER, MOD
- Logic: IF, TRUE, FALSE
- Lookup: VLOOKUP
- Text: CONCAT, LEFT, RIGHT, MID, LEN, UPPER, LOWER, TRIM
- Date: TODAY, NOW
Hope you enjoy. While I plan to continue polishing the UI/Expirence, it is not complete but is in a usable state. I will continue to iterate on the application as I continue with real world testing and data processing.
*Open to critique and suggestions for improvement!*
- @tdTrX@lemmy.ml
- •
- 11d
- •
Pros
Good Filtering and Easy and Free
Cons:
You tell a company your IP changes
Websites and tell your unique DNS

- •
- 10d
- •
Hello! DW is hosting another one of her no-cost 5-week degoogling challenges on Signal.
It's based mainly on the challenge she created [here](https://www.punchinguppress.com/post/shake-off-google-a-5-week-privacy-plan-infographic), but will be run by another member as she's slammed right now.
If you're interested, [request an invite into the group](https://signal.group/#CjQKIPfv-Xa5mSVIES2Rwx5-8tQHT8wgADjmXXAp6Glu23V-EhCM50toN-KpLV4lXJg1TM3Q).
- @tdTrX@lemmy.ml
- •
- 5d
- •
It's only visible on Android using special apps, not from OpenWRT next to it
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn’t great, if contents of the website are behind a paywall maybe copy them into the post
- Don’t promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
much thanks to @gary_host_laptop for the logo design :)
- 196 users online
- 108 users / day
- 435 users / week
- 1.32K users / month
- 4.54K users / 6 months
- 1 subscriber
- 4.67K Posts
- 118K Comments
- Modlog
Lemmy
A community of privacy and FOSS enthusiasts, run by Lemmy’s developers
Rules
- No bigotry - including racism, sexism, ableism, homophobia, transphobia, or xenophobia. Code of Conduct.
- Be respectful, especially when disagreeing. Everyone should feel welcome here.
- No porn.
- No Ads / Spamming.
Feel free to ask questions over in: