I just went to use nvcc for the first time and this nonsense hit my firewall. Make won’t compile but it has to do with my unwillingness to use the proprietary toolkit. This network activity only happened once on startup.
You must log in or register to comment.
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn’t great, if contents of the website are behind a paywall maybe copy them into the post
- Don’t promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
much thanks to @gary_host_laptop for the logo design :)
- 0 users online
- 108 users / day
- 435 users / week
- 1.32K users / month
- 4.54K users / 6 months
- 1 subscriber
- 4.57K Posts
- 115K Comments
- Modlog


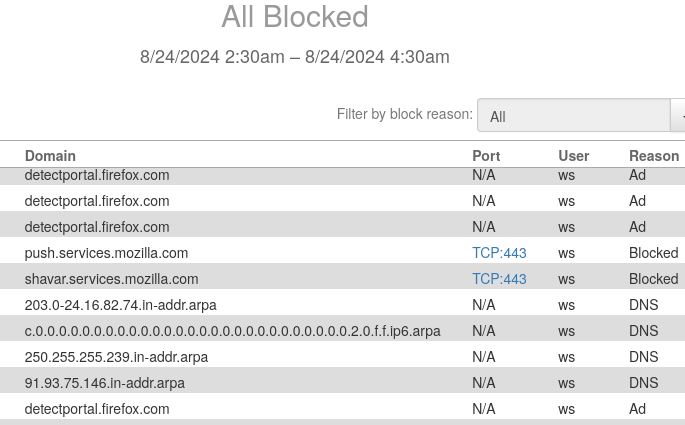




If you’re going to be looking at network requests on this granular of a level you should use something like OpenSnitch so you can be sure what is actually generating them.
Nothing concerning for me here personally. However, if you have an issue with Firefox’s ‘QoL’ features dependent on Mozilla infrastructure, you could consider Librewolf instead as an alternative.
As for the reverse lookup requests, those are targeting local multicast addresses on your internal network, except the last one which is for the Fastly CDN service
Does that sound like legitimate behavior for a compiler. I don’t consider such stalkerware data theft acceptable.
Both Librewolf and Firefox both have the QoL junk. Even after turning booth booleans off for Detect Portal, they still spam the messages constantly to let the host server know I’m still present and trackable, or whatever spin they try and put on that feature.
I have to admit I’m not entirely convinced these requests are coming from a compiler…
Is it possible for you to virtualize an non-networked system with your GPU passed through? That seems like the best option IMO. Next best thing would be to set up an airgapped machine just for this, but not everyone has a 2nd machine.
Personally when I was trying out local LLMs I used a virtual machine, mainly due to the known code execution vulnerability related to Tensorflow model data being saved in python’s Pickle format. I believe the recommended save method changed twice since those days though.
With the Firefox stuff I’m assuming you’ve also checked their enterprise config options too (which are admittedly difficult to find and piece together online), so not too sure what else you could do except aside from continuing to block them. Librewolf however provides documentation on how to disable the extra requests sent from their browser in their FAQ, and covers some preferences on the subsequent page linked at the bottom
Normally, I would be quite skeptical of what could be involved, and indeed my ability to diagnose the cause is limited. It is somewhat speculative to draw a conclusion. However, the machine is always behind this whitelist firewall, the only new software on the system was the llama.cpp repo and nvcc, and I’ve never encountered a similar connection anomaly.
I tried to somewhat containerize AI at first, but the software like Oobabooga Textgen defeated this in their build scripts. I had trouble with some kind of weird issue related to text generation and alignment. I think it is due to sampling but could be due to some kind of caching persistence from pytorch? I’ve never been able to track down a changing file so the latter is unlikely.
I typically only use regular FF for a couple of things, including Lemmy occasionally. Most of the extra nonsense on the log is from regular FF. Librewolf is setup to flush everything and store nothing. It only does a few portal checks an hour for whatever reason. I should look into stopping it. With regular FF I just don’t care or use it for much of anything. I just haven’t blocked it in DNF.
Detectportal I think is for knowing if your internet connection requires some sort of login. Like is that case in some hotels and airports
Yeah, the Firefox junk is just noise, the other 4 are the anomaly, especially those two IP addresses. Neither of those addresses are mine (yes I checked).
Looks like mostly multicast addresses