HyperSoop :spinny_cat_aroace: :spinny_fox_agender: (@soop@wetdry.world)
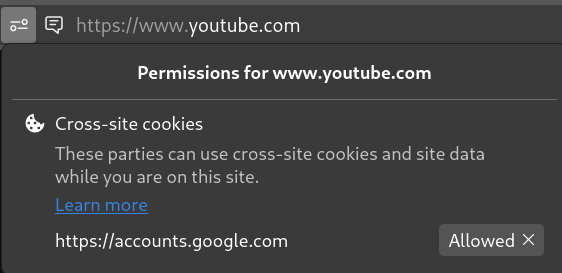
wetdry.worldDid you know? Despite claiming to block all cross-site cookies out of the box, Firefox automatically allows Google to use them in your browser should you log in to one of their services.
The browser only lets you know about this once it happens, and it’s on you to notice the permissions icon appearing in the URL bar. There is a link to a paragraph on a help page explaining this behaviour, but it seemingly goes unmentioned pretty much everywhere else on the internet.
This surprised me, especially considering Firefox’s stance on privacy. I was even more surprised that this is done without consent. If this is for usability, Firefox should at least warn the user before this happens.
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn’t great, if contents of the website are behind a paywall maybe copy them into the post
- Don’t promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
much thanks to @gary_host_laptop for the logo design :)
- 0 users online
- 108 users / day
- 435 users / week
- 1.32K users / month
- 4.54K users / 6 months
- 1 subscriber
- 4.57K Posts
- 115K Comments
- Modlog






Out of curiosity, do you know if these containers also obfuscate browser and device fingerprinting? Separating cookies is important but unless it also blocks fingerprinters (in a different way for each container) the site will instantly know the same person is using both accounts.
FF doesn’t really enable full fingerprint resistance by default. But it can.
These settings are some of what I usually use. All fingerprint values (that are able to be are randomised on every reload of a page.
Set secutity setting to custom, select known AND suspected fingerprinting > select from dropdown ‘In ALL tabs’
Also: Because it’s of no value / use to me, and (IMHO) a giant gaping privacy and security issue, I also disable webgl and webrtc, and navigator completely in about:config
Set the following:
WebGL webgl.disabled trueWebGL2 webgl.enable-webgl2 falseWebRTC media.peerconnection.enabled falseNavigator media.navigator.enabled falseRFP privacy.resistFingerprinting trueRFP options like bounce protection etc can also be enabled in config.
Check fingerprints on browserleaks.com, coveryourtracks.EFF.org, etc
Should be 100% unique fingerprint every time.