I wouldn’t recommend anything.
This is only what I know.
There is much much much more I don’t know.
This might be useful to use temporarily when you add an app that you know will read these values on install.
You may be able to use an app like geto to have this option toggled so that it only uses the developer settings option when the app is launched and returns to hardware when it closes.
Keep in mind there are a host of other identifiers on your device that can also be used to track and identify the user and device.
I like privacy and security.
So, the media DRM toggle switches from the hardcoded hardware ID to a software DRM. Creating a new DRM key.
https://developer.android.com/reference/android/media/MediaDrm

Geto uses shizuku (an app that allows for adb/shell functionality) to change settings that are usually hiddden or inaccessible, or to give/deny apps permissions or features, or, as in the screenshot to change certain keys values. This allows you to change the environment and settings of the app on launch, and revert them on app close.
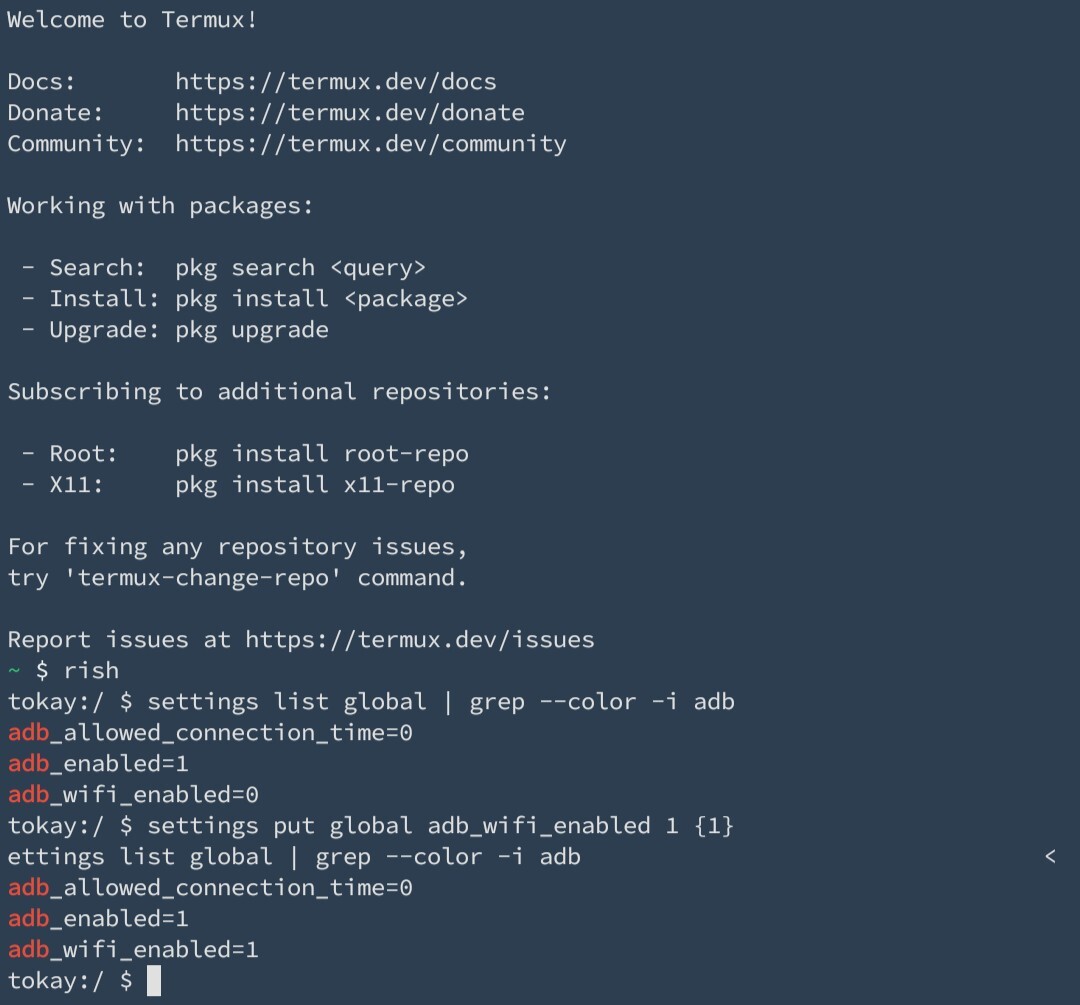
You can see all the current settings by using adb:
adb shell settings list [ global | secure | system ]
Or in termux with shizuku:
settings list [ global | secure | system ]
In the following screenshot I enter the shell using shizuku (rish) list global settings and find keys with adb. I change the value of adb_wifi_enabled (wirelese debugging) from 0 to 1 and set {1} as the default value. Then I list again to show the change.
This is what geto is doing. But it assigns it to the action of launching/closing an app. While doing it manually via terminal set those values system wide.
Sometimes, though, you may want a system wide change (like if you want to change the accent colors or theme from RAINBOW to VIBRANT).
(There are other configs and properties you can viewed and modify using other commands. (in shell try
cmd -l
For a list of services. Some have user modable options. Be careful. If you don’t know, don’t touch. Every setting can be searched . there are hundreds or thousands .)
Was able to get a different result using the media DRM toggle in developer settings

Verified results using TrustDevice
https://apt.izzysoft.de/fdroid/index/apk/com.trustdevice.android
https://www.trustdecision.com/
The other identifiers remained.
No appops or permissions change or prevent the exposure of other information.
Actually… Geto, can apply appop settings/values per app launch. And you can change the android_id value.

Remember when phones had that insane super advanced tech that could guide anyone anywhere, even offline?
Seriously, why doesn’t the compass exist anymore?
I have never turned on location anything on grapheme.
On my other phone I have also uninstalled google location services/history, WiFi scanning, Bluetooth unknown tracker, etc.
If I get lost in a building… I ask someone.
And I fucking quote myself in my comment above
distinction between foss and open source.
You said the comment in which I gave the fucking definition of Foss as written by the people who wrote the very definition of Foss was not foss.
You just gave me a link within the link that gives the definition of Foss about what Foss isn’t.
It isn’t me that needs to read better.
Go away.
You said what I posted was not Foss.
It came from the very essence of Foss.
It gave the very definition of Foss.
From the people who started Foss movement .
On the site run by the people who continue to promote and advocate for Foss.
And explains the distinction between Foss and open source.
What about that is unclear?
Post something else about open souce, please.
Tell me again how that is not what Foss is.
Please, guide me.
(What you cleverly replied with is in the link I posted ffs)
From itsfoss
It’s foss
https://itsfoss.com/what-is-foss/
Because GNU is Foss because Foss is gnu. Because the guy that started the fsf movement is Richard stallman who wrote that.
Maybe the people at the heart of Foss can make it more clear.
The free software movement campaigns to win for the users of computing the freedom that comes from free software. Free software puts its users in control of their own computing. Nonfree software puts its users under the power of the software’s developer
Free software means the users have the freedom to run, copy, distribute, study, change and improve the software.
Free software is a matter of liberty, not price. To understand the concept, you should think of “free” as in “free speech,” not as in “free beer.”
More precisely, free software means users of a program have the four essential freedoms:
The freedom to run the program as you wish, for any purpose (freedom 0). The freedom to study how the program works, and change it so it does your computing as you wish (freedom 1). Access to the source code is a precondition for this. The freedom to redistribute copies so you can help others (freedom 2). The freedom to distribute copies of your modified versions to others (freedom 3). By doing this you can give the whole community a chance to benefit from your changes. Access to the source code is a precondition for this.
My humble opinion
Example
Locked in google services. DNS so google sees the sites you visit, tracks what you click, where you go, who you talk to, what you like, what services you use, where you spend your money, etc.
Freedom - no log encrypted DNS rolling your own DNS server/proxy, seeing the config, the source; no tracking, no surveillance and profiles stored that are gladly shared with whatever other company or gov dept that wants it. No blobs or beacons. The ability to see what is happening, to choose what to allow or disallow, to be able to edit, modify, clone, fork, etc based on your needs and wants.
Not the Almighty profit margin.
Freedom to choose poison or antidote.
Another eg.
Nothing to hide may be true for now.
But what you believe need not be hidden, may, by some future government (or dictator), be deemed a crime, or worthy of retribution.
Allowing an unaccountable, unverifiable, monolith or shady actor is asking for problems.
The less data you share (or is unknowingly siphoned off) the less data you have to worry about being leaked /breached.
Knowing what is happening, being able to audit, being able to verify, freedom to choose vs blind trust.
If someone you don’t know knocks on your door, do you let them in and make themselves at home?
I use tor as a VPN (the tor org has finally realized and accepted people use it like this and welcome it now) via the tor network layer. I’ll run a few instances and run my stuff through them. (Easier to set up a conjure or webtunnel bridge and exit node to a specific country than rely on the randomness of tor browser where some countries have restrictions or are restricted from accessing certain sites.)
If I need that extra sense of anonymity, I’ll use the tor browser.
Ivpn is one service that not only supports the use of tor, but they also invest in the tor organization and run a lot of nodes.
Their site is also a goldmine of basic to advanced level docs on serious privacy and security (free). Including detailed instructions for cresting your own anon servers, vps, etc. And how to use a VPN with tor properly.
They are quite serious about what they do and how they do it.
You’ll be happy to know I just force killed :
Android system
Google services framework
Network
System UI
System WiFi Resources
Wi-Fi
Settings
System connectivity resources
Secure UI service
The results are the same
VPN kill switch prevents network access.
*later, when I’m connected to a PC, I’ll try killing/restarting userspace, shell, and user to see if I can get the kill switch to fail. (If I try those now it may kill shizuku which relies on shell - not sure.)
I’ll also see if I can’t force lmk to kill all the memory.
In cmd settings list secure these may be some part of what keeps the system from allowing a connection.
always_on_vpn_lockdown=1 always_on_vpn_lockdown_whitelist=

I just tested mull, Firefox, Firefox nightly, tor, and Vivaldi.
tor was the only one that produced results under 10 for every test. Except touch (70) screen (61k randomized anyway), and user agent (128 Firefox)
None of the tests produced an accurate result for screen -each one said my screen size had a different resolution.
Fingerprinting resistance randomizes or fakes certain api responses, as does a plugin like canvas blocker. So, those would definitely be higher numbers. But, they are always unique. Meaning they change. So it’s difficult to track.
If you try the same test and you’re unique EVERY TIME. That’s actually good.
But, there are things that can still be tracked if they stand out too much, and are static. (You can still be unique with static results in combination with randomization)
Like having a user agent “this is my phone”.
Too much customization / extensions makes you a giant orb of glowing user data.
Once a review ticket arrives in WhatsApp’s system, it is fed automatically into a “reactive” queue for human contract workers to assess. AI algorithms also feed the ticket into “proactive” queues that process unencrypted metadata—including names and profile images of the user’s groups, phone number, device fingerprinting, related Facebook and Instagram accounts, and more.
Does this also happen?
Author recommends a meta owned company for text messaging.
Lol.

Hmmm
Planting malware would violate the CFAA, 18 U.S.C. § 1030(a)(5)(A) (intentionally damaging through knowing transmission, imprisonment up to 10 years), as well as state computer crime laws.
The CFAA provides both criminal and civil penalties, and specifically prohibits: (1) unauthorised access (or exceeding authorised access) to a computer and obtaining national security information (imprisonment up to 10 years); (2) unauthorised access (or exceeding authorised access) to a computer used in interstate or foreign commerce and obtaining information (imprisonment up to one year); (3) unauthorised access to a non-public computer used by the United States government (imprisonment up to one year); (4) knowingly accessing a protected computer without authorisation with the intent to defraud (imprisonment up to five years); (5) damaging a computer intentionally or recklessly (imprisonment up to five years)
https://iclg.com/practice-areas/cybersecurity-laws-and-regulations/usa
Good thing laws don’t apply to the people who make the laws.
I am not. And I’ve never had this discussion.
Always on vs the additional option of blocking internet until the VPN connects.
The second option is more system level?
Using shizuku (rish) in termux I checked the active links with VPN on and then force stopped / killed the VPN in terminal and checked again. The VPN tunnel disappeared but the dummy kill switch tunnels remained. I could not access any network connection.
*The routing table also maintains the dummy kill switch

BTW, thanks for these posts.
Sadly moz Dev is … Difficult to find info about things other than the function and how to call it. The source is all there, and some things are buried so deep in some topic or obscure inaccessible part of their site. But practical functionality and actual results of use are difficult to determine on my lonesome.
I use the tests on https://librewolf.net/docs/testing/ to do some things, but there are just so many unknowns.
Thanks again.

Regarding tab isolation etc, do you know if in about:config setting the storage partitioning (by site, proxy, eyc) and/or disabling automatic storage access makes a difference? There are options for strict site isolation in there, too, but I don’t know if toggling one thing will break another.
Also, don’t containers on FF on Linux do that?
browser.discovery.containers.enabled
privacy.usercontext.enabled
Nico was a mistake, I meant to link another site. Granted. You can look for yourself that it was thiel who called for the run on the bank. https://www.axios.com/2023/03/14/founders-fund-run-silicon-valley-bank
But bilderberg group is real. Very real. (They had a meeting here, once https://www.cbc.ca/news/canada/ottawa/kanata-hotel-hosts-high-level-power-group-1.601298 )
And thiel is president.
Also, if you can find his manifesto (I’m having a hard time locating it ) he openly states everything i said.
Also :
https://time.com/6092844/peter-thiel-power-biography-the-contrarian/
Thiel taught this class at Stanford and then turned it into a book called Zero to One. He talks about how companies are better run than governments because they have a single decision maker—a dictator, basically. He is hostile to the idea of democracy. That’s pretty scary when you consider the role the companies that he’s been involved in play. Facebook, I’d say is the most influential media entity in the history of humanity, but he also has a major stake in several defense contractors, including SpaceX
Brave is the offspring of “libertarian” (sociopathic authoritarian billionaire supporting JD Vance) Peter Thiel.
https://marketrealist.com/p/who-owns-brave-browser/
Thiel, among other things, founded palantir, facial recognition software used by police worldwide.
https://www.palantir.com/platforms/
He hates the western world. Hates democracy.
https://www.politico.com/magazine/story/2016/11/donald-trump-steve-bannon-peter-thiel-214490/
Openly states his plans to destroy the economy and implement a crypto financial system.
https://www.axios.com/2023/03/14/founders-fund-run-silicon-valley-bank
And, this is true, he’s the current president of the bilderberg group.
https://www.bilderbergmeetings.org/meetings/meeting-2024/participants-2024
He is not your friend.
He should never be trusted.
Brave is not the private browser you think it is.
By supporting brave you are supporting an authoritarian technocratic state.

OOTB Firefox is a security and privacy concern.
But it allows for nearly unlimited tweaking, modding, blob removal, etc. Which many serious threat model browsers are based on. Eg Tor.
If the Tor browser is less secure than chromium, there are potentially devastating consequences for some very at risk people.
Will you be analyzing forks such as tor and mull?

FF doesn’t really enable full fingerprint resistance by default. But it can.
These settings are some of what I usually use. All fingerprint values (that are able to be are randomised on every reload of a page.
Set secutity setting to custom, select known AND suspected fingerprinting > select from dropdown ‘In ALL tabs’
Also: Because it’s of no value / use to me, and (IMHO) a giant gaping privacy and security issue, I also disable webgl and webrtc, and navigator completely in about:config
Set the following:
WebGL webgl.disabled true
WebGL2 webgl.enable-webgl2 false
WebRTC media.peerconnection.enabled false
Navigator media.navigator.enabled false
RFP privacy.resistFingerprinting true
RFP options like bounce protection etc can also be enabled in config.
Check fingerprints on browserleaks.com, coveryourtracks.EFF.org, etc
Should be 100% unique fingerprint every time.

Yes.
I have a google container for one account.
If I open a google site in another container it will be as if the account didn’t exist.
The containers are all partitioned.
You can also partition off the cookie/storage per site by proxy used (in about:config).
So, you could create a container for google account 1 using proxy 1 and another container for google account 2 using proxy 2 and they will never have access to the data stored by either.


Seems the only real solution is to buy cheap burners.
Curious if using the website version of an app can pick up the mediaDRM key via the browser.