edit: please see comments for more informed insights.
I am currently investigating and reverse engineering free VPNs for a master thesis, and just came across something I thought I’d share. VPN in this case is 1clickvpn.net, not .com!
I’m sharing this as a warning as to never use free vpns! They are most often the opposite of what they promise to be. (by free I do not mean the free versions of premium services). But either way; be careful about your VPN choice, as they have access to a lot of sensitive data. I’m sure most peeps here know of this already, but next time you hear someone using a free vpn, let them know…
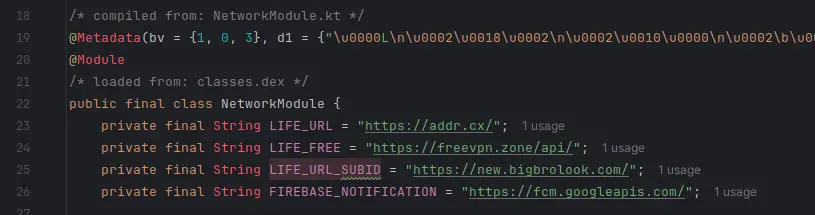
This first image/code was sitting inside a file called NetworkModule, with some hella weird external links.
- addrDOTcx, seems to have been linked to malware? Comes up flagged as malicious a few times on VirusTotal.
- freevpnDOTzone, seems to be another free possible malicious VPN service, might investigate this one later.
- bigbrolookDOTcom, seems to longer be a registered domain. But wtf? Was this VPN service linked to p*rn??
IMAGE HERE; Don't visit these links unless you know what you're doing.
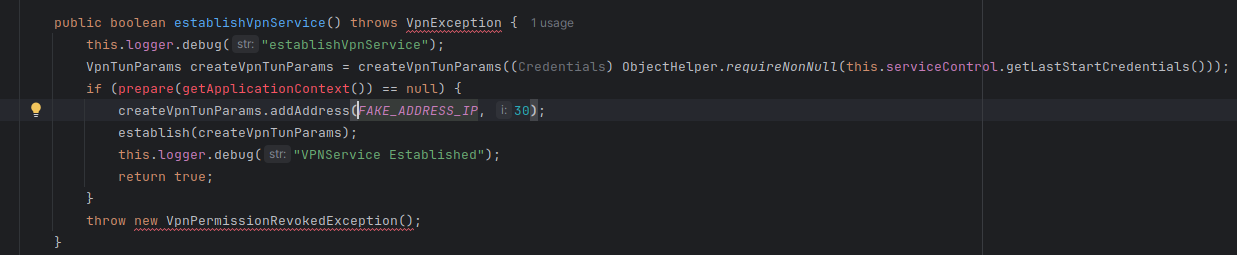
Furthermore, there is this interesting find; Now I am no expert coder, frankly quite the amateur. But does the below code really mean what I think it does? Seems like it could be creating a fake connection?. This is more-less normal behaviour it seems, considering it is a local address it is probably used for testing purposes or making the app not crash if a connection cant be established.
 Is used once here;
Is used once here;
Stay safe 🌻
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn’t great, if contents of the website are behind a paywall maybe copy them into the post
- Don’t promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
much thanks to @gary_host_laptop for the logo design :)
- 0 users online
- 108 users / day
- 435 users / week
- 1.32K users / month
- 4.54K users / 6 months
- 1 subscriber
- 4.62K Posts
- 116K Comments
- Modlog






Thank you for doing the work. More of it needs to be done. I don’t know what your workflow is, but running Android-x86 and injecting into the virtualbox networking process to strip the SSL should still work, unless the app uses certificate pinning. I wish I remembered the name of the program, but it’s specifically for injecting into a running exe and hooking all network calls to pull ALL network data from that specific app. It’s not Fiddler or Wireshark or any of those. Fiddler and wireshark will work fine if you add your self-signed cert to the Android CA list, as long as certificate pinning isn’t used in the app. You can point wireshark to the virtualbox network adapter so it doesn’t listen on your other adapters. Also, most apps in the app store, play store, and F-Droid likely will not have much maliciousness. Play Store has the highest chance. But I think you’ll have better luck using all the major search engines and searching for “free VPN android” without any adblockers, using an android phone (Google & co easily detect user-agent manipulation) running chroming. Making note of all the paid ads, and then getting the first 10 pages of URLs, and then comb those links (all the ad links & result links) and download any .apk that shows up. Keep an eye out for more ads on those pages as well. Use a fresh android-x86 for each analyzed VPN apk.
There may be a better, easier way, but this was how I quickly analyzed the network data of android malware as of a few years ago.
Edit: other keywords to find shady vpns are ads for things like “watch porn in Utah” and “express VPN”, " nord VPN", etc. You’ll want to do the search within android as Google and Bing will allow the malvertisers to target specific operating systems, along with locations and other variables.
Also for checking into the servers that show up, and any interesting domains, you can use shodan and similar tools, and there is a great site (name escapes me now, similar to domaintools and urlscan.io though) that shows what domains run on certain IP addresses and also the owners and creation dates, although cloudflare and private whois entries make those less useful today. But that will potentially allow you to unmask ‘networks’ of shady free VPN providers.
urlscan is a good tool for checking server basic information.
Thanks for this, will definitely incorporate some of this into my workflow!