


I use cloudflared to translate DNS into DNS over TLS instead of Unbound to make it into recursive DNS. Just never really seen the need to switch it. I’m happy with nextDNS + Cloudflare resolving DNS upstream.
The main thing I wanted to note is port 53 outbound is blocked at the router to prevent devices from using external/unencrypted DNS. If a LAN device wants DNS resolution they MUST use the LAN DNS servers they were given via DHCP, or use their own DoT config, as plain DNS won’t make it out of the network.
It’s because of this block/enforcement that I run two local DNS servers: pihole on an RPI and a mirror on my main server tower, with Galaxy-Sync keeping them identical. If I tinker with/update one, the other picks up the slack so connectivity/resolution isn’t disrupted.
It’s google; their entire business is built on fucking you out of your personal data. Once they have it, they will never let go.
Until a highly scrutinized third party audit proves otherwise; I doubt even GDPR removal requests are complied with internally. They might stop telling you they have the data, but thetly won’t actually get rid of it.


You could use something like DroidCam to make your phone available as a web cam on your pc, then capture it with OBS or similar. Use a vpn to keep the devices on the same network.
You’d either have to leave the pc recording all the time or use remote desktop to start the recording.
Another option is to look at software to turn your pc into an NVR and find an app that essentially lets you use your phone like an IP Security Camera. Again, using a VPN to keep them in the same network.


You can redirect regular DNS like that, but DoH/DoT is encrypted using certificates with a chain of trust just like any other tls connection (that’s kind of the whole point). It would throw security errors breaking dns resolution if you redirected the connection to your own server.
You would still be better off with a vpn wrapping the connection however as the SNI in each https connection is unencrypted and can be used to log your traffic.


Copy of my comment in c/apple:
Honestly I think this is the right move.
Pull the feature and tell the public that the government won’t permit the public to secure their own data.
“I have security and privacy features for you, but your government won’t let you use them”
Set the public against this overreach.
This is exactly what nextDNS is doing:
1sc5k91u2kx-2e5621.test.nextdns.io
Showed up in my dns logs when I opened the page, with a new random number each refresh.
Regular DNS can be monitored, intercepted, and modified however your ISP decides, even with you specifying custom DNS servers.
I run pihole on my LAN, with cloudflared as its upstream DNS. Cloudflared translates regular DNS into DOH using cloudflare and quad9 as the upstream DOH providers (configurable).
Finally I block all port 53 (dns) traffic at the router so it cannot leave my LAN. All LAN devices that want regular DNS are forced to use the LAN DNS server which wraps their requests in DOH for them. (as well as blocking ads, tracking/telemetry, and known malware sites)
https://github.com/mozilla-mobile/firefox-ios/pull/16545
Reader mode loads the page from a local copy cached from the non-reader mode connection; via localhost, which doesn’t support https. (or rather, uses a self-signed cert which appears insecure). As this connection is entirely internal to the device, proper https isn’t necessary.
Later versions of the app will hide that icon in reader mode, but it doesn’t look like that’s made it to android yet.


I’ve never felt the need to use a VPN at home. I’m not really trying to hide from my own ISP, nor obfuscate where my connections come from.
I do host my own VPN from my home network though. This allows me to access my self-hosted services without exposing them directly to the internet, as well as keeps my mobile devices behind my pihole dns servers so they always receive dns adblocking and access to private dns records (self-hosted stuff). This also keeps mobile traffic a bit more secure from snooping, particularly on public/corporate wifi networks.
BorgBackup creates compressed and de-duplicated backups, splitting data into chunks then only keeping unique chunks + a list of files those chunks belong too.
I’ve currently got around 470gb being backed up; compression brings that down to 320gb, then after de-duplication that’s down closer to 70gb. (there’s a lot of media metadata in there, results will vary)
17 backups going back 6 months: 8.10 TB original > 5.62 TB compressed > 326.55 GB final backup data stored on disk
/edit this thread is a week old… It showed up at the top of my ‘new’ feed…? Odd.
https://docs.pi-hole.net/guides/dns/cloudflared/
I use pihole+cloudflared to translate all DNS requests on my LAN to DoH requests. Regular DNS isn’t permitted to leave my network. (port 53 outbound is blocked)
Can’t redirect/modify/monitor DoH requests like you can plain DNS.


Repost: https://feddit.uk/post/16382677
It’s barely been two days…


The default Samsung Calculator doesn’t display a privacy policy (or any menu options really) in-app, but you can find them as a link at the bottom of the ‘See Details’ page under ‘Data Saftey’ on the play store. Annoyingly, it’s just a generic set of terms that covers most of their products/services. That document says they collect and share all sorts of data, but the store page for the calculator say no data collected.
Two piholes at home (redundancy). Those both translate all regular DNS requests to DoH using Cloudflared which rotate through 4 non-isp upstream DoH providers.
The router is set to block all port 53 traffic from leaving the network and handout the 2 pihole IPs to dhcp clients for dns. If a LAN device wants regular dns, it MUST use the lan servers or it’ll get no response. (or it can use its own DoH setup and/or vpn out of the network). This enforces the ad/telemetry/malware blocking lists pihole uses without having to configure dns on everything.
Those piholes also keep lists/records in sync using Gravity-Sync. Should I change ad lists or add/remove lan dns records, I don’t have to do it on both.
If you’re looking for an ad-free client that still works right now; In the 6 years I’ve been using YouTube (re)vanced on android, I’ve only had it fail to play videos for 1 single day around 6 months ago. That was fixed within 24hrs.
Not quite the same as a full custom instance/frontend like piped; but it’ll do the job while you wait for updates.
They are more secure than password authentication, though how much more secure depends on how the user manages their passwords.
If a user never reuses passwords across different services and maintains long complex passwords, preferably randomized strings; the security upgrade of Passkeys is quite marginal. Arguably marginal enough to not even bother. The farther a user gets from ‘ideal’ password security practices though, the more of a security upgrade Passkeys would be for them; though convincing them of that is another story…
Switching to Passkeys does take a lot of responsibility off of both the user and service provider. The user no longer needs to ensure passwords aren’t reused, insufficiently complex, or already compromised; and the service provider doesn’t need to worry about leaking your passkey as they only have the public key portion which can’t be used to login as you.
In some ways they can be more inconvenient though. With a password, even long unique complex passwords stored in my password manager; I can open the password manager on my phone, read the password I want, and manually enter it into an unfamiliar or shared device without having to load my entire password/key vault onto that device. Passkeys make that impossible; essentially forcing you provide the whole vault to the device or give up. It is also a big step for people that aren’t familiar with password managers and are used to just remembering their passwords, to then switch to a passkey manager where they can’t use their memory to login anymore.
There’s good sides and bad sides to everything really. Some people will prefer one way, some will want the other way. Ultimately I think we’ll get pushed into using Passkeys by most companies, just so they can shed some of the responsibility of keeping your credentials secure. A stolen passkey database, unlike a password database, would not allow you to pose as users, which leads to less claims of fraudulent activity.


Yup, Swedish police issued a search warrant and raided Mullvads offices last year. They left empty handed as Mullvad does not retain ANY customer data.


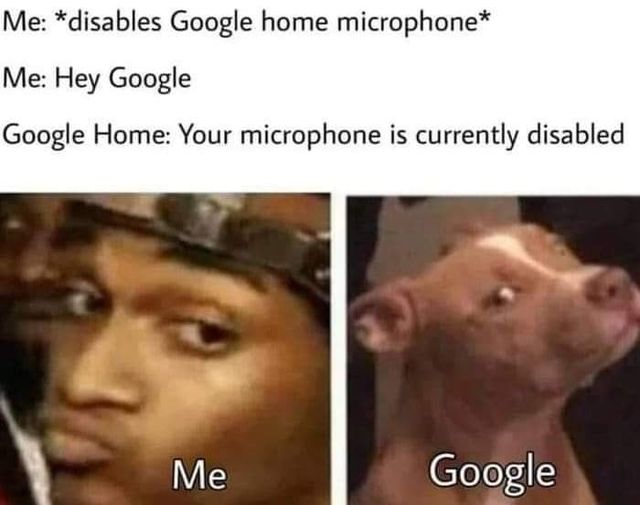
The microphone disable switch on every google home/amazon alexa device does not physically disable the microphone; it just informs the software that you’d like it to not listen to you. It can still do so whenever it pleases.
This is how/why it is able to respond ‘your microphone is currently disabled’ when you try to command it with that switch on.


I specify my LAN DNS servers (2 pihole instances, main + a backup for redundancy) in my routers DHCP settings, so they are the DNS servers handed out to all LAN clients; then I have an iptables rule on the router blocking all port 53 traffic from leaving the network unless it came from those LAN DNS servers. This means only the piholes can reach external dns; everything else is required to use the LAN DNS servers or receive no response. Then the piholes have full control over what can and cannot resolve to an IP.
I haven’t found a device that doesn’t work with this setup. I used to have a couple google homes before I wised up, they worked fine behind this setup.


Reminds me of this doc I watched a couple weeks ago.
TLDW; psyco travelled across the country to kill his mom, then drove back. He bought a burner phone at the start of his trip, but kept his normal phone with him the whole time. The cops were able to track both devices as they each connected to the same cell towers while traveling together from the west coast, to the east coast, and back again.
Why would you ever be buying a sim card seprate from the carrier servicing it…?
Honestly asking, that’s incredibly unusual to me. Where I live, the mobile carrier always provides the sim card. Usually free with a monthly phone plan, or as a part of a pre-paid plan. (pre-paid you can usually buy from a corner store like seven eleven. monthly you’ll actually have to visit their store/mall booth)


Meh, just Mullvad. Cops can raid em all they want; they just walk away empty handed


That makes no sense.
We aren’t talking about two phones paired with each other, were talking about a pair of headphones or a smart watch, causing the phone it’s linked to to make a sound. Nothing more.
There is absolutely 0 opportunity to acquire a location from that.
Beyond that; apple products, specifically airpods and apple’s smart watch, have these abilities.
Why would it be a security flaw to allow an Apple manufactured device to perform these functions, but not a third party device, utilizing the exact same implementations?
Try again.

https://openwrt.org/
I’ve never personally used that one, but it gets recommended a lot.
I’ve been using DD-WRT for 15+ years, but that’s for no particular reason other than It’s what I found first and haven’t had any reason to switch.