Heya, I found how you can digitally sign and encrypt emails! (It even gives them a cool icon for others to see!), and I haven’t seen anything about it before so I thought I’d share how I did it!
Do you also want to send encrypted emails and sign them? Just follow these few steps!
But beforehand, let’s define some terms :
-
Signed email : Email with a valid numerical signature. Anyone can read it and know it has not been modified since it was sent.
-
Encrypted email : Email encrypted with the recipient’s public key. They can decrypt it with their private key
-
S/MIME certificate : A
.p12file containing your private key (So keep it for yourself and don’t send it to anyone!!) and your public key.
Okay, now it’s time to…
Start the setup (Obtain an S/MIME certificate)
- You’ll need to ask to an authority for a certificate. Personally I use Actalis because they give free certificates for multiple email addresses, valid for a year (you need to redo the setup every year). If you don’t want to use Actalis, more info is avilable here.
- Don’t forget to put the website in english if you don’t understand italian.
- Go on the page to request an S/MIME certificate, create an account and follow the setup. The verification email can take a little while (~2min)
- When the setup ends, you’ll have a valid certificate in your dashboard (It can take a few minutes to appear if you just verified it) that you can download, and a password that Actalis emailed you to enable your certificate.
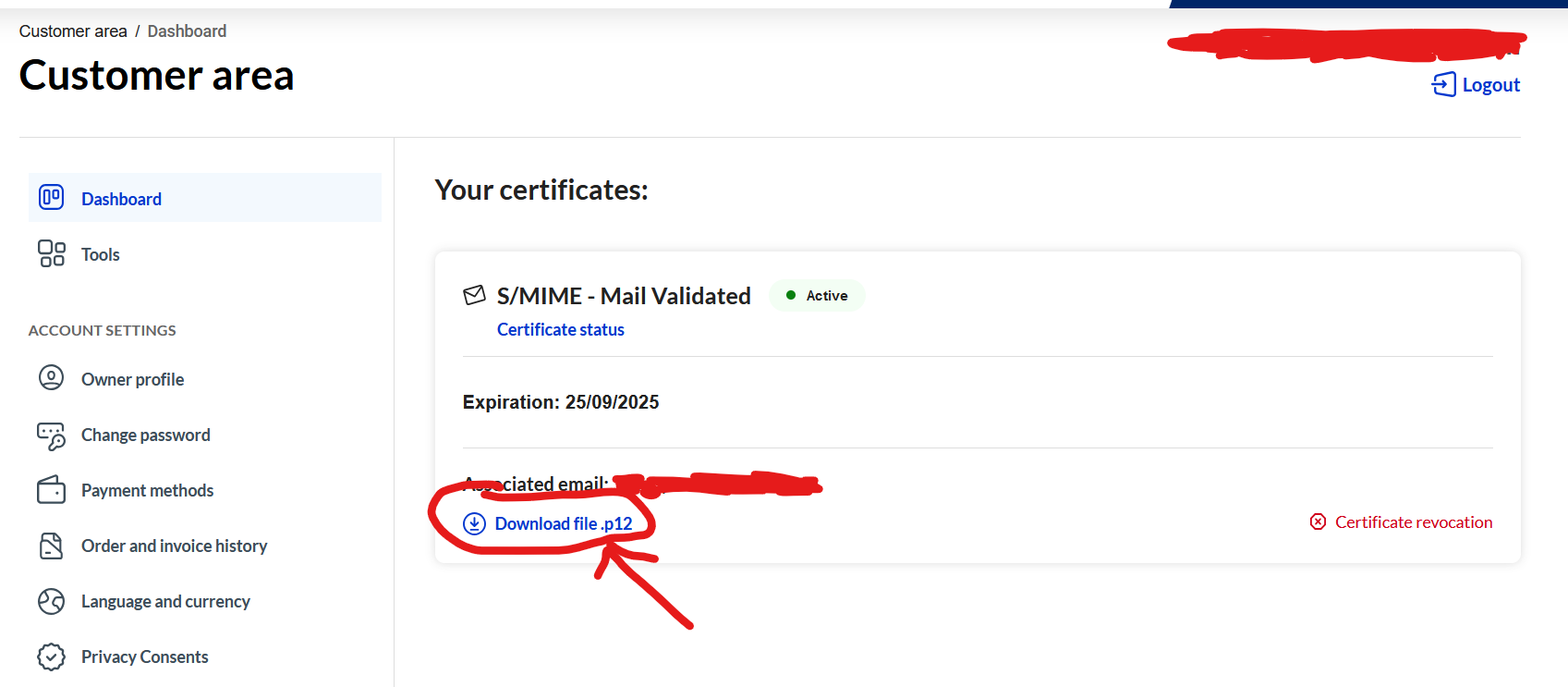
Install the certificate
- Download the .p12 file, then open it, type your password, and leave the default options to install the certificate on your device (Android or PC, on Android pick “For VPN and apps”). Don’t delete your old one, so you can still decrypt old messages sent on the expired certificate
- Use an S/MIME compatible email client. On PC, there is Thunderbird, on Android, FairEmail.
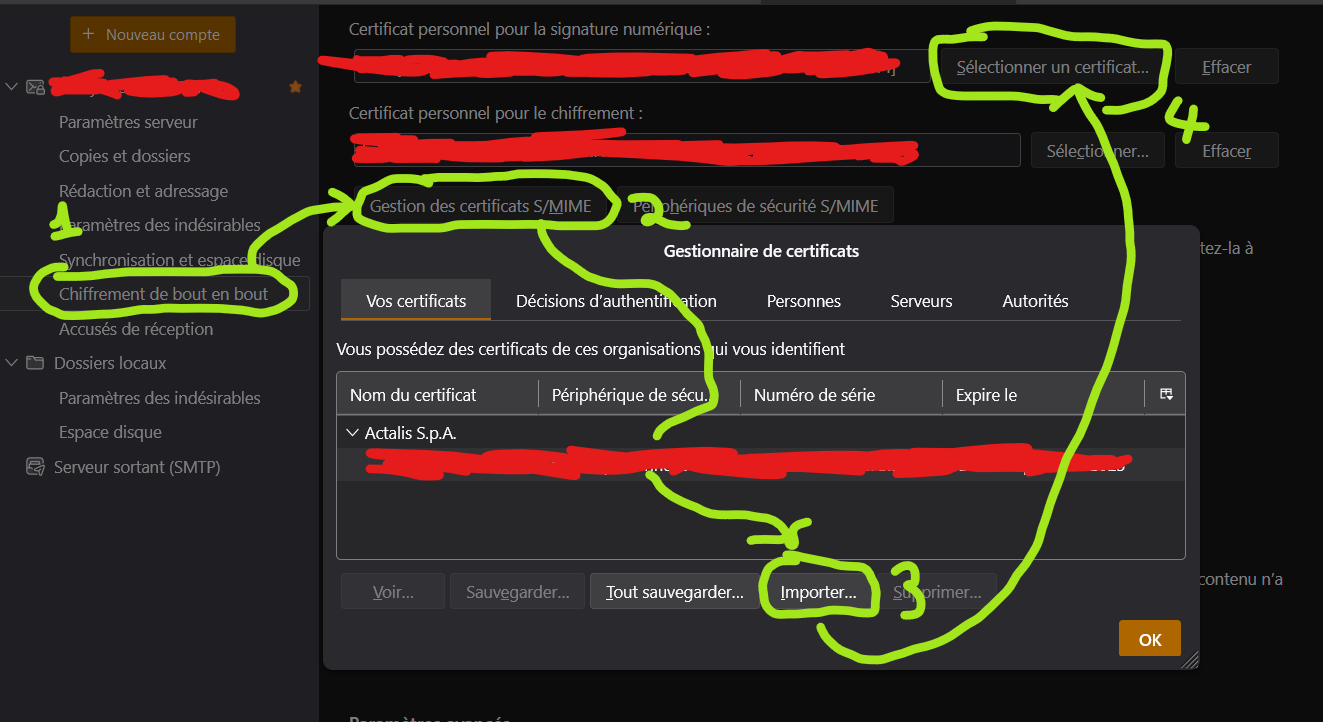
- In your email client settings, importer the S/MIME certificate pofor signing AND encrypting your messages. It changes depending on your client, so here it is for Thunderbird :
- In the top-right menu, go to
Account settings,End-to-end encryption, underS/MIMEclick onManage S/MIME certificates,Importand pick your.p12file. Then, pickSelect a certificate, and pick yours from the tab “Your certificates”.
- In the top-right menu, go to
An image is worth a thousand words (Sorry for the french)
Don’t forget to check the box to sign and/or encrypt every message just below, if you want!
Communicate with someone
Once this is done, here is how you can communicate…
- …While signing your messages :
It’s easy, just click on “Sign” before sending. Usually, email clients show a small medal next to your name to show the email is signed.
- …While encrypting your messages :
For that, you’ll need your recipient’s public key. They needs to send you a signed message (not encrypted, since you don’t have each other’s key at this point) where you can get their public key from their signature, and add it to your email client, which will allow you to encrypt messages you send to them. Then, send them a signed email (you can encrypt it) so they can get your public key and add it to their client, and then you’ll be able to exchange encrypted emails!
I’m not an expert and probably made a few mistakes, if you spot any please tell me in the comments and I’ll try to fix the guide!
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn’t great, if contents of the website are behind a paywall maybe copy them into the post
- Don’t promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
much thanks to @gary_host_laptop for the logo design :)
- 0 users online
- 108 users / day
- 435 users / week
- 1.32K users / month
- 4.54K users / 6 months
- 1 subscriber
- 4.61K Posts
- 116K Comments
- Modlog






Be aware, that trusted Certificate Authority (CA) configuration applies to ALL certificates issued by CA. Thus, if one elects to trust “actalis” CA, then they trust ALL actalis CA users.
If the process of obtaining certificate was extremely simple, easy and did not involve identity verification steps, then bad actors can take advantage of this process and create identities that your client application will trust.
By itself the bad actor identity is of little concern to anybody, but it can have a significant impact if trusted identity is used in spam filtering, exploits of email client bugs or other hack attempts. Trusted users may be given higher access privilege at the client application level, which may be just enough for hacker to gain required access. For example, client application may be configured to trust all trusted senders with MIME attachments. An unknown trusted user sends malicious Application as file attachment. Accidental double click lunches the application without “are you sure?” prompt. Congratulations, machine is pwned.
The problem is easily mitigated by not importing root CA for easy CAs.