
With dumbphones, you’re usually limited to regular phone calls or SMS/MMS messaging.
That’s kind of the point.
Sure, you can’t do much with them, but by that very fact you also won’t have nearly as much data to be spied on.
Likewise, you can do much more with a smartphone, but that comes with a much higher surface of attack, and you also have to work a lot harder to keep all the data away from spying.


Honestly, it might be I’m wrong about this since I don’t live in a big city so maybe it’s different in like NYC or some shit, but I’m under the impression that QR Codes have kinda been dead in the US. At least I hardly ever see one in the wild anymore. Mainly I presume for that reason. It’s a prime way for malware injection.


Apple Maps -OSMandMaps. Seems like a good option, but it’s not ready out the box. I need to do more tweaking with it. -Magic Earth. Haven’t tested it yet, seems good. But I’m looking for free options first before I dabble with paid stuff.
If you like OSM but want a more user-friendly interface (disclaimer: I’m an Android user so I have no idea what OSMandMaps looks like), check out CoMaps! It was forked from Organic Maps due to heavy transparency concerns surrounding the former and uses downloadable OSM maps as a backend! It’s available for iOS too!
https://www.comaps.app/download/
Google Docs -OnlyOffice. Seems like it does everything I want.
I’ve heard OnlyOffice is great, but if you don’t need or want any AI stuff, don’t mind a slightly less-modern UI, and collaboration isn’t a requirement, then LibreOffice is pretty awesome too. Just giving you another option. ;)


Okay, so, originally, I was going to look it up to prove you wrong, but after looking it up across multiple sources, it seems that you’re right and I’m wrong.....mostly.
How-To Geek, Proton, and CloudFlare all mirror what you say.
However, the Wikipedia page section “Definitions” does back me up somewhat. It says:
The term “end-to-end encryption” originally only meant that the communication is never decrypted during its transport from the sender to the receiver.[23] For example, around 2003, E2EE was proposed as an additional layer of encryption for GSM[24] or TETRA,[25] ... This has been standardized by SFPG for TETRA.[26] Note that in TETRA, the keys are generated by a Key Management Centre (KMC) or a Key Management Facility (KMF), not by the communicating users.[27]
Later, around 2014, the meaning of “end-to-end encryption” started to evolve when WhatsApp encrypted a portion of its network,[28] requiring that not only the communication stays encrypted during transport,[29] but also that the provider of the communication service is not able to decrypt the communications ... This new meaning is now the widely accepted one.[30]
(Relevent text is embolded.)
So, I’m not misunderstanding, just misinformed that the definition changed.
Make no mistake, of course: I do appreciate you correcting me as I hadn’t realized the definition had changed. Lol.


I mean it’s in the name. A message containing media and not text is simply not a text message. Many people use them incorrectly but it’s literally in the name.
Hey, I get it now. Lol. I was just explaining what my mindset was.
RCS is (supposedly) E2EE so keys are stored locally.
Well, you can have E2EE with keys stored server-side. It’s just kind of pointless from a security/privacy standpoint, but I’ve seen it happen.


MMS is not a text message, it’s a media message (that’s what the M stands for).
See, that’s interesting because I was always taught that “text message” is just an overarching term used to describe SMS and MMS. The notion that a text message is a synonym of SMS and only SMS is a new one to me!
Yes, RCS chats are encrypted (supposedly)
Good to know! Do you happen to know if the decryption keys are stored offline or on the carrier’s end? Because if the latter, then okay it’s more secure than SMS or MMS but only in the sense that some encryption is better than none. Lol.


Oh cool.
Yeah, in Eternal, it seemed that once I got past the first few areas, if I didn’t do glory kills, I’d be, within seconds, nearly dead and almost completely out of ammo (if not out of ammo).
You’re saying Doom 2016 isn’t like that.
Like, don’t get me wrong, glory kills are awesome, but I feel they should be optional flairs to spice up gameplay, not a required function just to progress. That’s what bothered me. It effectively locked out of the game (a Doom game no less) anyone who didn’t like the glory kill mechanic. Personally, as a long-time fan of the franchise, that felt kinda cheap.


Just be aware people that–and this should surprise no one as these features are largely online nowadays (sadly no LAN here :C )—but...
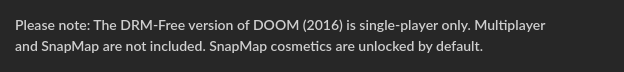
That being said, I personally won’t be buying this. Not because the game is poorly made or anything (it’s Doom–'nuff said); I’m just not really into the whole glory kill thing. Don’t like it.
No shade to anyone who does; that’s just my opinion.


Oof, yeah I forgot about the metadata… What you say is certainly true and is worrisome.
Plus, most people who use email don’t use encrypted email so even if they can’t get a transcript of a conversation from my account, they can certainly get everything from the other account if they also scrape that platform.


Proton
Signal
What are they gonna do? Download gibberish?! Lol, it’s all end-to-end encrypted with the decryption keys stored locally.
Edit: See below comment by @drascus@sh.itjust.works. Shit’s still concerning.


OF COURSE they called them domestic terrorists. That’s what all authoritarian regimes call groups that are a threat to them. 🙄