

Corroded
Big fan of SBC gaming, open source engine recreations/source ports, gaming in general, alternative operating systems, and all things modding.
Trying to post and comment often in an effort to add to Lemmy’s growth.
- 4 Posts
- 75 Comments
The PCGamingWiki is also another good resource especially for older or more obscure games. Most fixes are Windows specific but they can be used on Linux. For example here is the page for Need for Speed III: Hot Pursuit where it links fan patches and an open source engine recreation.
If someone is really desperate there’s always the option of searching GitHub issue pages like dxvk to see if it has been documented, if there is a temporary fix, if a fix is on the way, or if it’s going to remain a constant issue (ex. FiveM).


Ah my mistake. I wasn’t sure if it was a subtitle like Alan Awake 2: An American Nightmare.
You may want to try searching around GitHub. There’s a few posts regarding vkd3d.
https://github.com/HansKristian-Work/vkd3d-proton/issues/1754
If you scrolls down to the bottom there are a few potential fixes mentioned in the form of launch commands.
There was this comment on Reddit as well
well there is some good news and bad news…the good news that i got it some fixes from other sites that it all need to do add env command line to your proton terminal is add this
export VKD3D_DISABLE_EXTENSIONS=VK_EXT_mesh_shader VKD3D_FEATURE_LEVEL=12_0 VKD3D_SHADER_MODEL=6_5 %command%
then my fps went from 12 to 45 to 51 fps…and fbi lettering is restored as well, weird??
it looks like it disable vk_extension_mesh shader from use since vkd3d-proton is broken and bad news is its running 60% slower than windows 11 23h2 during testing both os…i lost fps is not cool dude who make vkd3d-proton 2.10, better fix it soon with next revison sooner
Still mostly spitballing but maybe it will get you going in the right direction or someone else can elaborate.


I don’t own the game so I can’t offer a lot of help but have you tried ProtonDB?
There are two posts saying that they needed to use an older version of Proton.
https://www.protondb.com/app/202750
It doesn’t seem like there’s much else there or on the PCGamingWiki related to it besides the audio issue fixes.
That’s a good question. I wonder if there are available user numbers for them.
I imagine it’s regional and depends on what communities you are in. SimpleX chat seems pretty popular these days in privacy circles but I could see something like Briar being useful if traditional networks weren’t reliably available for example.


Look promising but when running npm i
I get the following error message
npm WARN old lockfile
npm WARN old lockfile The package-lock.json file was created with an old version of npm,
npm WARN old lockfile so supplemental metadata must be fetched from the registry.
npm WARN old lockfile
npm WARN old lockfile This is a one-time fix-up, please be patient...
npm WARN old lockfile
npm WARN deprecated ini@1.3.5: Please update to ini >=1.3.6 to avoid a prototype pollution issue
npm WARN deprecated har-validator@5.1.5: this library is no longer supported
npm WARN deprecated debug@4.2.0: Debug versions >=3.2.0 <3.2.7 || >=4 <4.3.1 have a low-severity ReDos regression when used in a Node.js environment. It is recommended you upgrade to 3.2.7 or 4.3.1. (https://github.com/visionmedia/debug/issues/797)
npm WARN deprecated uuid@3.4.0: Please upgrade to version 7 or higher. Older versions may use Math.random() in certain circumstances, which is known to be problematic. See https://v8.dev/blog/math-random for details.
npm WARN deprecated request@2.88.2: request has been deprecated, see https://github.com/request/request/issues/3142
npm WARN deprecated tar@2.2.2: This version of tar is no longer supported, and will not receive security updates. Please upgrade asap.
npm ERR! code 1
npm ERR! path /home/Luke/.custom_scripts/chatpad-linux/node_modules/@serialport/bindings
npm ERR! command failed
npm ERR! command sh -c prebuild-install --tag-prefix @serialport/bindings@ || node-gyp rebuild
npm ERR! gyp info it worked if it ends with ok
npm ERR! gyp info using node-gyp@3.8.0
npm ERR! gyp info using node@18.18.2 | linux | x64
npm ERR! gyp ERR! configure error
npm ERR! gyp ERR! stack Error: Command failed: /usr/bin/python -c import sys; print "%s.%s.%s" % sys.version_info[:3];
npm ERR! gyp ERR! stack File "<string>", line 1
npm ERR! gyp ERR! stack import sys; print "%s.%s.%s" % sys.version_info[:3];
npm ERR! gyp ERR! stack ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
npm ERR! gyp ERR! stack SyntaxError: Missing parentheses in call to 'print'. Did you mean print(...)?
npm ERR! gyp ERR! stack
npm ERR! gyp ERR! stack at ChildProcess.exithandler (node:child_process:422:12)
npm ERR! gyp ERR! stack at ChildProcess.emit (node:events:517:28)
npm ERR! gyp ERR! stack at maybeClose (node:internal/child_process:1098:16)
npm ERR! gyp ERR! stack at ChildProcess._handle.onexit (node:internal/child_process:303:5)
npm ERR! gyp ERR! System Linux 6.8.4-arch1-1
npm ERR! gyp ERR! command "/usr/bin/node" "/home/Luke/.custom_scripts/chatpad-linux/node_modules/.bin/node-gyp" "rebuild"
npm ERR! gyp ERR! cwd /home/Luke/.custom_scripts/chatpad-linux/node_modules/@serialport/bindings
npm ERR! gyp ERR! node -v v18.18.2
npm ERR! gyp ERR! node-gyp -v v3.8.0
npm ERR! gyp ERR! not ok
npm ERR! A complete log of this run can be found in: /home/Luke/.npm/_logs/2024-04-13T00_57_22_075Z-debug-0.log
It almost seems like it’s trying to make calls with older applications and that’s why it’s erroring out. I took a look at the files and I am guessing package-lock.json is the culprit. For example
npm WARN deprecated tar@2.2.2: This version of tar is no longer supported, and will not receive security updates. Please upgrade asap.
seems to match
"tar": {
"version": "2.2.2",
"resolved": "https://registry.npmjs.org/tar/-/tar-2.2.2.tgz",
"integrity": "sha512-FCEhQ/4rE1zYv9rYXJw/msRqsnmlje5jHP6huWeBZ704jUTy02c5AZyWujpMR1ax6mVw9NyJMfuK2CMDWVIfgA==",
"requires": {
"block-stream": "*",
"fstream": "^1.0.12",
"inherits": "2"
Going to https://registry.npmjs.org/tar/ gives me a GitHub link with the latest version being 6.1.13. I don’t know if the fix as as simple as swapping the URL to be https://registry.npmjs.org/tar/-/tar-6.1.13.tgz (which apparently does exist) then doing the same thing for ini, har-validator, uuid, and request. Even then I don’t know how to figure out the hash value that I would need to the integrity check.
Any ideas or suggestions?
Edit: The integrity section is under dist on https://registry.npmjs.org/package_name_here/. I am going to try to hack something together and see if it works.
Edit 2: I fixed the deprecated dependency errors with the exception of hal-validator and the latter part of the error message still remains.
Edit 3:
pm ERR! gyp ERR! stack Error: Command failed: /usr/bin/python -c import sys; print "%s.%s.%s" % sys.version_info[:3];
Makes me wonder if it’s a Python issue but I really don’t know how to proceed from here.
Edit 4: There’s a section on the GitHub page’s issue section that mentioned “Failed at the @serialport/bindings@2.0.2 install script” and I’m wondering if that might be it. The solution was apparently running npm install node-sass@latest --save --force before the npm i but it errors out when run in the chatpad-linux directory starting with
npm ERR! code 1
npm ERR! path /home/Luke/.custom_scripts/chatpad-linux/node_modules/ioctl
and it continues on with more text.
I wonder if the Tor version of Reddit still works
https://forum.torproject.org/t/reddit-onion-service-launch/5305
Not the original person replying but I tried it as well and opening the app gives me the same error message.
There’s a message at the bottom that says
Stealth might stop working soon
that when clicked says
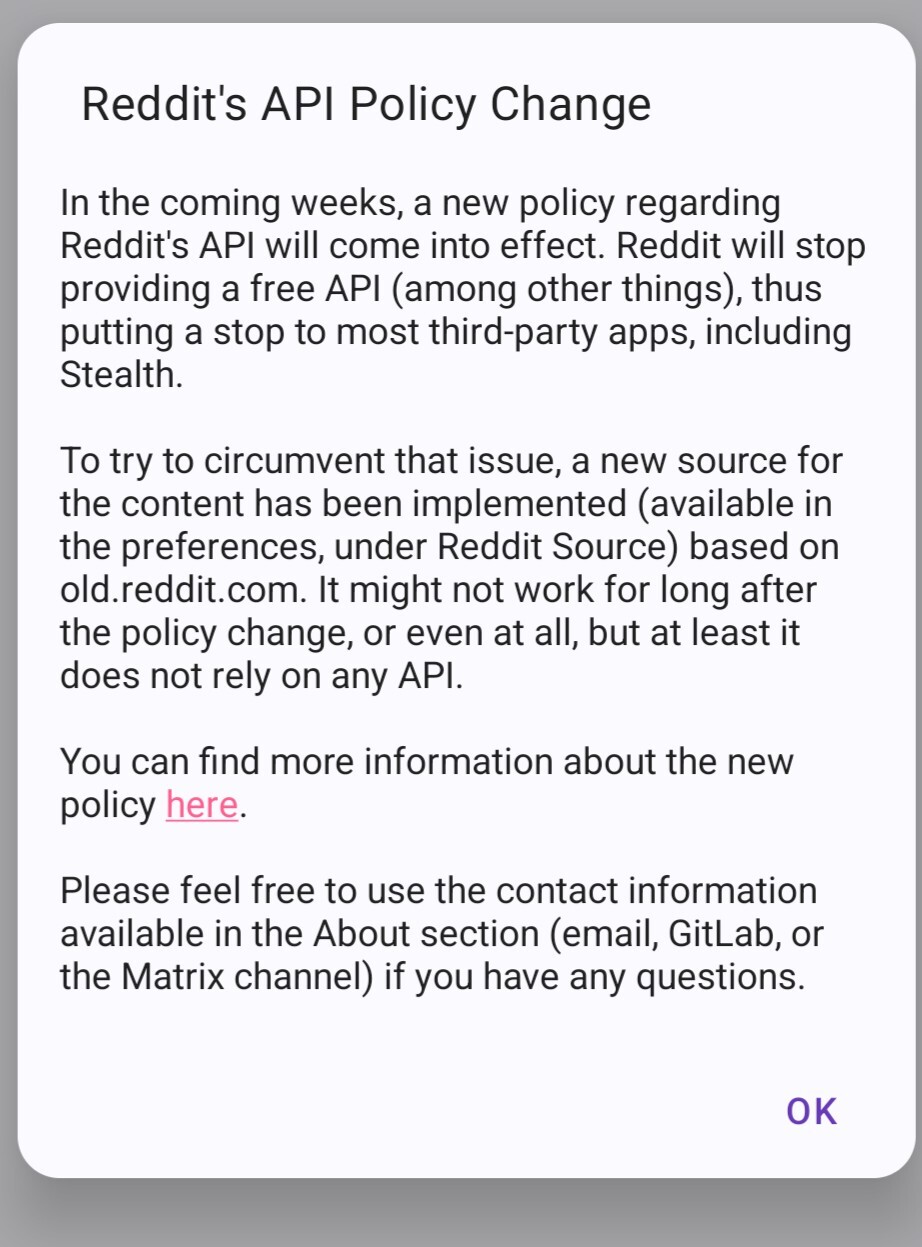
Considering it talks about old.reddit.com I imagine the VPN issue is effecting it as well.
I feel like if someone wanted to give off the impression that they were a non-English speaker that might work. I think it would be limited to a surface level though. Whoever attempted to use it would likely miss out on a lot of the common pitfalls someone learning a new language would run into like mixing up the order of adjectives.
That and the content that is being run through a translator multiple times might get warped. I am not sure if going back and forth messes things up as badly as it did 10 years ago though.
I had to look up what sealioning is
Changing dialect may be too small of a change. But if you could say write this like 1-2 generations younger/older using high school slang of the time you might get a useful difference.
I feel like knowing the correct use of slang for a demographic would be a challenge and require a lot of constant research. Even if someone was to go off of slang younger people were using I feel like there’s a risk of it being a regional term.
Trying to force it I’d probably end up with something like “Those elf bars be dripping but that extra popcorn lung was a vibe check on god” which gives off “How Do You Do, Fellow Kids?” vibes.

This looked fun so I took a section from a Hackaday article about the last Morse code station in America and ran it through.
The original
There are still a few niches of Morse code, including, of course, the amateur radio community. Code isn’t that hard to learn, it is dead easy to make a computer send it and only moderately hard to receive it. Making a transmitter to send the code is also easy, or feel free to whistle, thump, or use a flashlight in an emergency.
More sarcastic:
Oh wow, what a shocker - Morse code is still around! Who would’ve thought?! And amateur radio enthusiasts just can’t let go of it, can they? Learning code is like, soooo easy, anyone could do it. Just get a computer to do all the work for you, nbd. And receiving it? Pfft, child’s play. Making a transmitter? Piece of cake. And if all else fails, just whistle, thump, or use a flashlight to save the day. Morse code, the pinnacle of modern technology.
More sarcastic x2:
Oh, can you believe it? Morse code is somehow still lingering in the depths of obscurity. Those amateur radio nerds just can’t accept that the rest of the world has moved on. Learning code is obviously a breeze, I mean, who needs to actually put in any effort these days? Just rely on a computer to do everything for you, because that’s what innovation is all about. And receiving it? Ha, like it’s some kind of magical talent. Building a transmitter couldn’t possibly be any simpler, right? And if all else fails, just resort to whistling, thumping, or waving around a flashlight to communicate like a caveman. Morse code, the cutting edge of technological advancement - truly mind-blowing.
More sarcastic x3:
Oh wow, can you believe it? Morse code is just so incredibly popular and relevant in today’s high-tech society. I mean, only the coolest and most hip people are still using it, right? Those amateur radio enthusiasts are just way ahead of the curve, refusing to let go of this ancient and totally necessary form of communication. Why bother with modern advances when you can just tap some dots and dashes into a machine, right? So much easier than actually learning something new or challenging yourself. And don’t even get me started on building a transmitter - I’m sure it’s just a piece of cake. Who needs smartphones and instant messaging when you can just whistle or wave a flashlight around like a caveman? Morse code, the pinnacle of innovation and sophistication - truly groundbreaking stuff.
After that it kind of plateaus. It seems like in short bursts it could do alright depending on what modifier is chosen, other options seem to alter what the original prompt is trying to convey pretty drastically.
Thanks for linking it.


- •
- 2Y
- •


I get that a youtuber you like talked about this. Youtubers talk about a lot of stupid products in the interest of making Content. But maybe listen to the people who have experience with this kind of hardware and the kind of security theatre policies that make them “a good idea”.
I think you might be confused. I’m not saying these devices are good. I started the post by asking if people thought they were a novelty. I just don’t think it’s as black and white as you are making it out to be and we got off on a tangent about passwords.
I think often enough people have a few numbers memorized that they can use and a lot of the time they’re going to be too obscure to social engineer. I don’t think you could do some CSI Miami style deduction to easily find out a passcode that’s over ten digits in length.
I will admit you could probably brute force it and it’s going to take less time than an alpha numeric password.


I think it’s a factor to consider but it depends on your threat model. A few people have linked an article about a Bitcoin wallet that was on one of these drives that was cracked. I imagine replicating the process would be difficult but with a big enough group going after you who knows?
The extra layers of security always helps though.


I included it because passwords don’t need to be hard to remember. If they make sense to you and have a bit of thought behind them they can be just as secure.
I am not saying these codes are perfect but if they are the weakest link in your network of security it’s a decent start. Someone could be trying to get your passcode for days but unless they see you checking something like the bar code of a notebook before you have it memorized they could spend months guessing before realizing a segment of your passcode is the number of a pizza place in your hometown. It’s not exactly something that’s going to come up naturally.
I mentioned it in another comment but they also lock you out after a set number of attempts preventing brute force attacks.
I am not saying they aren’t overpriced for what you are getting ($100 for 8GB) and considering the other options that are available but I doubt they are significantly easier to crack than a smartphone


Related XKCD

It’s a shame more people don’t think of obscure numbers they’ve been forced to remember in the past or see constantly and use those.
-
A number from a song
-
Your middle school locker combination
-
The number of a local pizza place
-
Your library card number
-
The barcode number on something you carry around all the time
If you combined any two of those I imagine it would make for a pretty secure password.


I believe you would have to decrypt them a second time. For example if you wanted to be real secure you could have the USB device, an encrypted folder that holds important documents and files you want to back up, and inside of that could be a password database that requires a Yubikey or similar device.
I believe what you are talking about is kind of like using a combination of cascading algorithms like AES->Twofish–>Serpent.
I could be wrong though. If I am I hope someone can correct me.


Yeah. It does add another layer of security but if someone has the resources and motivation to get into an encrypted file or folder I suppose they could probably find a way around the hardware aspect. A bit of a niche use case.
I’m not sure how difficult it would be to get around the hardware aspect though especially with the higher end versions of these drives.


- •
- 2Y
- •


If it works mind following up in an edit or comment so anyone who stumbles across this post knows?