Voluntarily sharing informative posts from unaffiliated sources.
- 21 Posts
- 2 Comments
Joined 10M ago
Cake day: Jan 16, 2024
- PayPal to Share Shopping Details
- LinkedIn Opts You In for AI Data Sharing
- 23andMe May Sell Your DNA Data
>A [new Federal Trade Commission (FTC) report](https://www.ftc.gov/news-events/news/press-releases/2024/09/ftc-staff-report-finds-large-social-media-video-streaming-companies-have-engaged-vast-surveillance) confirms what EFF has been warning about for years: tech giants are widely harvesting and sharing your personal information to fuel their online behavioral advertising businesses. This four-year investigation into the data practices of nine social media and video platforms, including Facebook, YouTube, and X (formally Twitter), demonstrates how commercial surveillance leaves consumers with little control over their privacy. While not every investigated company committed the same privacy violations, the conclusion is clear: companies prioritized profits over privacy.
>
>While EFF has long warned about these practices, the FTC’s investigation offers detailed evidence of how widespread and invasive commercial surveillance has become.
[Here are key takeaways from the report](https://www.eff.org/deeplinks/2024/09/ftc-report-confirms-commercial-surveillance-out-control)
LinkedIn scraped user data for training AI before updating its terms of service and without obtainin
>LinkedIn users in the U.S. — but not the EU, EEA, or Switzerland, likely due to those regions’ data privacy rules — have an opt-out [toggle](https://www.linkedin.com/mypreferences/d/settings/data-for-ai-improvement) in their settings screen disclosing that LinkedIn scrapes personal data to train “content creation AI models.” The toggle isn’t new. But, as first [reported](https://www.404media.co/linkedin-is-training-ai-on-user-data-before-updating-its-terms-of-service/) by 404 Media, LinkedIn initially didn’t refresh its privacy policy to reflect the data use.
>The terms of service have now been [updated](https://www.linkedin.com/legal/privacy-policy), but ordinarily that occurs well before a big change like using user data for a new purpose like this. The idea is it gives users an option to make account changes or leave the platform if they don’t like the changes. Not this time, it seems.
>**To opt out of LinkedIn’s data scraping, head to the “Data Privacy” section of the LinkedIn settings menu on desktop, click “Data for Generative AI improvement,” then toggle off the “Use my data for training content creation AI models” option. You can also attempt to opt out more comprehensively [via this form](https://www.linkedin.com/help/linkedin/ask/TS-DPRO), but LinkedIn notes that any opt-out won’t affect training that’s already taken place.**
>The nonprofit Open Rights Group (ORG) has called on the Information Commissioner’s Office (ICO), the U.K.’s independent regulator for data protection rights, to investigate LinkedIn and other social networks that train on user data by default.
>“LinkedIn is the latest social media company found to be processing our data without asking for consent,” Mariano delli Santi, ORG’s legal and policy officer, said in a statement. “The opt-out model proves once again to be wholly inadequate to protect our rights: the public cannot be expected to monitor and chase every single online company that decides to use our data to train AI. Opt-in consent isn’t only legally mandated, but a common-sense requirement.”
For Android users seeking a privacy-focused browser, [Privacy Guides](https://www.privacyguides.org/en/mobile-browsers/#mull) recommends Mull:
>Mull is a privacy oriented and deblobbed Android browser based on Firefox. Compared to Firefox, it offers much greater fingerprinting protection out of the box, and disables JavaScript Just-in-Time (JIT) compilation for enhanced security. It also removes all proprietary elements from Firefox, such as replacing Google Play Services references.
>Mull enables many features upstreamed by the Tor uplift project using preferences from Arkenfox. Proprietary blobs are removed from Mozilla's code using the scripts developed for Fennec F-Droid.
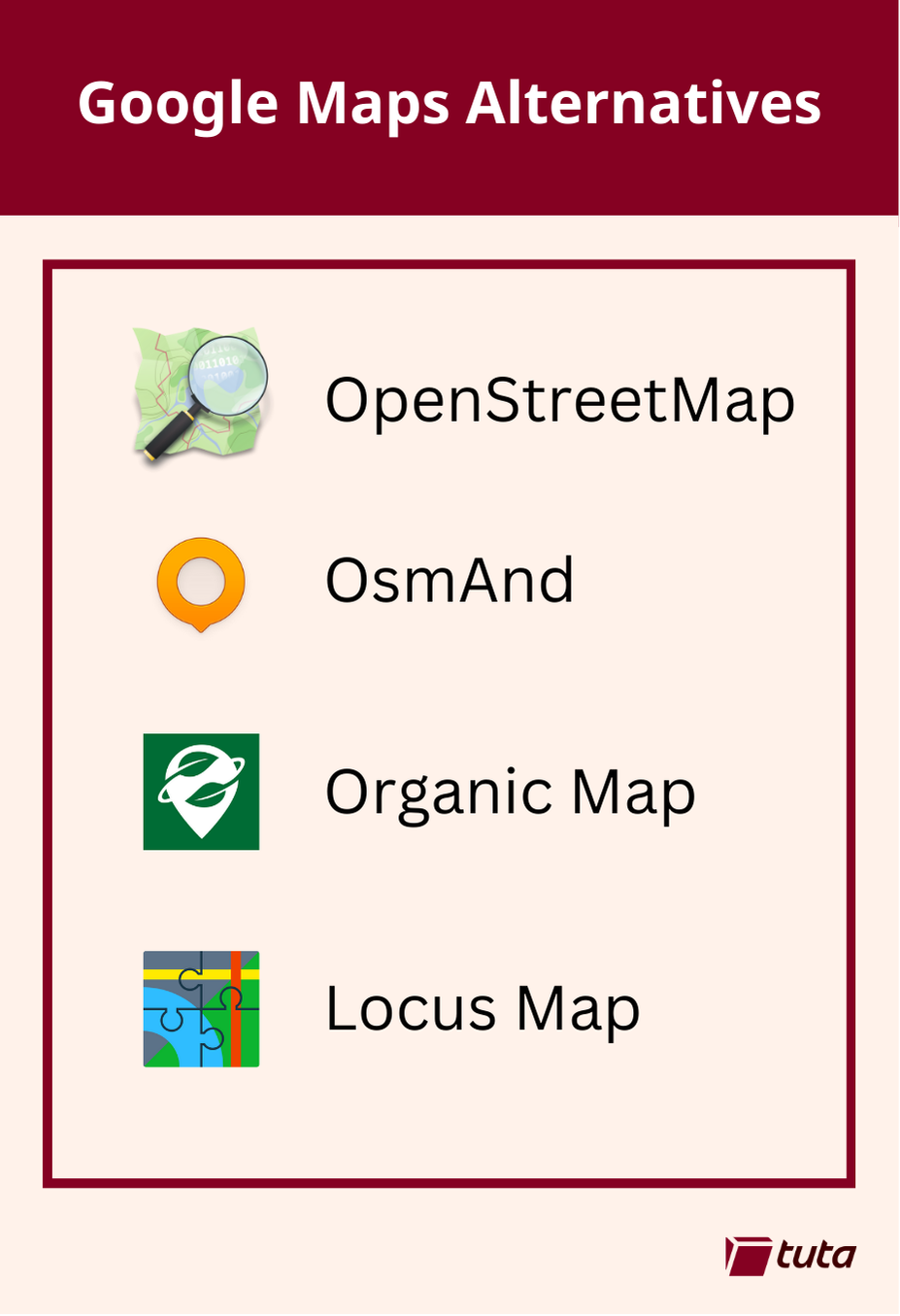
>repeated media reports of Google’s disregard for the privacy of the general public led to a push for open source, community driven alternatives to Google Maps. The biggest contender, now used by Google’s direct competitors and open source projects alike is OpenStreetMap.
1. OsmAnd
>
>OsmAnd is a fantastic choice when searching for an alternative to Google Maps. It is available on both Android and iOS devices with both free and paid subscription options. Free accounts have full access to maps and navigation features, but choosing a paid subscription will allow you unlimited map downloads and increases the frequency of updates.
>
>All subscriptions can take advantage of turn-by-turn navigation, route planning, map markers, and all the favorite features you expect from a map and navigation app in 2024. By making the jump to a paid subscription you get some extra features like topo maps, nautical depths, and even point-of-interest data imported from Wikipedia.
2. Organic Maps
>
>Organic Maps is a great choice primarily because they offer support for all features of their iOS and Android apps completely offline. This means if you have an old phone laying around, you can install the app, download the maps you need and presto! You now have an indepth digital map in the palm of your hand without needing to worry about losing or damaging your primary mobile device when exploring the outdoors.
>
>Organic Maps tugs our heartstrings by their commitment to privacy. The app can run entirely without a network connection and comes with no ads, tracking, data collection, and best of all no registration.
3. Locus Maps
>
>Our third, and last recommendation today is Locus Maps. Locus Maps is built by outdoor enthusiasts for the same community. Hiking, biking, and geocaching are all mainstays of the Locus App, alongside standard street map navigation as well.
>
>Locus is available in its complete version for Android, and an early version is available for iOS which is continuing to be worked on. Locus Maps offers navigation, tracking and routes, and also information on points-of-interest you might visit or stumble upon during your adventures.
>Filed in 2022, the Texas lawsuit said that Meta was in violation of a state law that prohibits capturing or selling a resident’s biometric information, such as their face or fingerprint, without their consent.
>The company announced in 2021 that it was shutting down its face-recognition system and delete the faceprints of more than 1 billion people amid growing concerns about the technology and its misuse by governments, police and others.
>Texas filed a similar lawsuit against Google in 2022. Paxton’s lawsuit says the search giant collected millions of biometric identifiers, including voiceprints and records of face geometry, through its products and services like Google Photos, Google Assistant, and Nest Hub Max. That lawsuit is still pending.
>The $1.4 billion is unlikely to make a dent in Meta’s business. The Menlo Park, California-based tech made a profit of $12.37 billion in the first three months of this year, Its revenue was $36.46 billion, an increase of 27% from a year earlier.
>The Kids Online Safety Act (KOSA) easily passed the Senate today despite critics' concerns that the bill may risk creating more harm than good for kids and perhaps censor speech for online users of all ages if it's signed into law.
>KOSA received broad bipartisan support in the Senate, passing with a 91–3 vote alongside the Children’s Online Privacy Protection Action (COPPA) 2.0. Both laws seek to control how much data can be collected from minors, as well as regulate the platform features that could harm children's mental health.
>However, while child safety advocates have heavily pressured lawmakers to pass KOSA, critics, including hundreds of kids, have continued to argue that it should be blocked.
>Among them is the American Civil Liberties Union (ACLU), which argues that "the House of Representatives must vote no on this dangerous legislation."
>If not, potential risks to kids include threats to privacy (by restricting access to encryption, for example), reduced access to vital resources, and reduced access to speech that impacts everyone online, the ACLU has alleged.
>The ACLU recently staged a protest of more than 300 students on Capitol Hill to oppose KOSA's passage. Attending the protest was 17-year-old Anjali Verma, who criticized lawmakers for ignoring kids who are genuinely concerned that the law would greatly limit their access to resources online.
>"We live on the Internet, and we are afraid that important information we’ve accessed all our lives will no longer be available," Verma said. "We need lawmakers to listen to young people when making decisions that affect us."
>In a new academic paper, researchers from the Belgian university KU Leuven detailed their findings when they analyzed 15 popular dating apps. Of those, Badoo, Bumble, Grindr, happn, Hinge and Hily all had the same vulnerability that could have helped a malicious user to identify the near-exact location of another user, according to the researchers.
>While neither of those apps share exact locations when displaying the distance between users on their profiles, they did use exact locations for the “filters” feature of the apps. Generally speaking, by using filters, users can tailor their search for a partner based on criteria like age, height, what type of relationship they are looking for and, crucially, distance.
>To pinpoint the exact location of a target user, the researchers used a novel technique they call “oracle trilateration.”
>The good news is that all the apps that had these issues, and that the researchers reached out to, have now changed how distance filters work and are not vulnerable to the oracle trilateration technique.
>Neither Badoo, which is owned by Bumble, nor Hinge responded to a request for comment.
Archive link: https://archive.ph/GJauG
>In exchange for selling them repair parts, Samsung requires independent repair shops to give Samsung the name, contact information, phone identifier, and customer complaint details of everyone who gets their phone repaired at these shops, according to a contract obtained by 404 Media. Stunningly, it also requires these nominally independent shops to “immediately disassemble” any phones that customers have brought them that have been previously repaired with aftermarket or third-party parts and to “immediately notify” Samsung that the customer has used third-party parts.
>Aaron Perzanowski, a personal property law expert and professor at the University of Michigan Law School, told me “Most consumers would be very surprised to learn that their personal information and details about their devices are being shared with the manufacturer. And I doubt there is any meaningful disclosure of or consent to sharing that data. So this looks like a substantial and unexpected invasion of consumer privacy.”
>“This is exactly the kind of onerous, one-sided ‘agreement’ that necessitates the right-to-repair,” Kit Walsh, a staff attorney at the Electronic Freedom Foundation and right to repair expert told me. “The data collection is excessive. I may not have chosen to disclose my address or identity to Samsung, yet an added cost of repair—even at an independent shop—is giving that information up. In addition to the provision you mentioned about dismantling devices with third-party components, these create additional disincentives to getting devices repaired, which can harm both device security and the environment as repairable devices wind up in landfills.”
>Political campaigns tap into the same intrusive adtech tracking systems used to deliver online behavioral ads. We saw a glimpse into how this worked after the Cambridge Analytica scandal, and the system has only grown since then.
>In 2020, Open Secrets found political groups paid 37 different data brokers at least $23 million for access to services or data. These data brokers collect information from browser cookies, web beacons, mobile phones, social media platforms, and more.
>These political data brokers make a lot of promises to campaigns. TargetSmart claims to have 171 million highly accurate cell phone numbers, and i360 claims to have data on 220 million voters. They also tend to offer specialized campaign categories that go beyond the offerings of consumer-focused data brokers. Check out data broker L2’s “National Models & Predictive Analytics” page, which breaks down interests, demographics, and political ideology—including details like "Voter Fraud Belief," and "Ukraine Continue." The New York Times demonstrated a particularly novel approach to these sorts of profiles where a voter analytics firm created a “Covid concern score” by analyzing cell phone location, then ranked people based on travel patterns during the pandemic.
>As streaming video services integrate more ad-based subscription tiers, that likely means more political ads this year. One company, AdImpact, projects $1.3 billion in political ad spending on “connected television” ads in 2024.
>Political ad spending on Google (mostly through YouTube) is projected to be $552 million, while Facebook is projected at $568 million.
>Managing the flow of all this data might feel impossible, but you can take a few [important steps](https://www.eff.org/deeplinks/2024/04/how-political-campaigns-use-your-data-target-you) to minimize what’s out there. The chances you’ll catch everything is low, but minimizing what is accessible is still a privacy win.
>The EU's Data Protection Board (EDPB) has told large online platforms they should not offer users a binary choice between paying for a service and consenting to their personal data being used to provide targeted advertising.
>In October last year, the social media giant said it would be possible to pay Meta to stop Instagram or Facebook feeds of personalized ads and prevent it from using personal data for marketing for users in the EU, EEA, or Switzerland. Meta then announced a subscription model of €9.99/month on the web or €12.99/month on iOS and Android for users who did not want their personal data used for targeted advertising.
>At the time, Felix Mikolasch, data protection lawyer at noyb, said: "EU law requires that consent is the genuine free will of the user. Contrary to this law, Meta charges a 'privacy fee' of up to €250 per year if anyone dares to exercise their fundamental right to data protection."
- Academics at the University of Pennsylvania analyzed a nationally representative sample of 100 non-federal acute care hospitals – essentially traditional hospitals with emergency departments – and their findings were that 96 percent of their websites transmitted user data to third parties.
- Not all sites had privacy policies and of those that did, only 56% disclosed specific third parties receiving data.
- Google and Meta (through Facebook Pixel) were on nearly every site and received the most data. Adobe, Verizon, Oracle, Microsoft, Amazon also received data.
- Common data shared included IP addresses, browser info, pages visited, referring site.
- Sharing data poses privacy risks for visitors and legal/regulatory risks for hospitals if policies don't comply with laws.
- A class action lawsuit against Mass General Brigham and Dana-Farber resulted in an $18.4M settlement over sharing patient data.
- Researcher calls for hospitals to collaborate with computer science departments to design more private websites. Also recommends privacy tools to block third party tracking.
>But in the meantime, and in lieu of any federal data privacy law in the US, protecting personal information falls to the individual. And for that, Friedman recommends browser-based tools Ghostery and Privacy Badger, which identify and block transfers to third-party domains. "It impacts your browsing experience almost none," he explained. "It's free. And you will be shocked at how much tracking is actually happening, and how much data is actually flowing to third parties."
**Note**: Although Friedman recommends Ghostery and Privacy Badger, [uBlock Origin](https://github.com/gorhill/uBlock#readme) is generally considered a better privacy-enhancing browser extension. Additionally, there exist [multiple approaches](https://avoidthehack.com/how-to-block-ads) for adblocking and tracker blocking beyond the browser extension model.
**The purpose of this post is not to endorse the use of Reddit ([](https://tosdr.org/en/service/194)), but rather to inform users of a privacy-friendly approach in case they need to utilize the platform.**
Redlib is a private front-end like [Invidious](https://github.com/iv-org/invidious) but for Reddit.
- 🚀 Fast: written in Rust for blazing-fast speeds and memory safety
- ☁️ Light: no JavaScript, no ads, no tracking, no bloat
- 🕵 Private: all requests are proxied through the server, including media
- 🔒 Secure: strong [Content Security Policy](https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP) prevents browser requests to Reddit
- Self-hostable
Redlib currently implements most of Reddit's (signed-out) functionalities but still lacks [a few features](https://github.com/redlib-org/redlib/issues).
### Redlib [Instances](https://github.com/redlib-org/redlib/blob/main/README.md#instances)
(If a particular instance doesn't work, try others to see if they work)
|URL|Network|Version|Location|Behind Cloudflare?|Comment|
|-|-|-|-|-|-|
|https://safereddit.com|WWW|v0.31.0|🇺🇸 US||SFW only|
|https://l.opnxng.com|WWW|v0.31.0|🇸🇬 SG|||
|https://libreddit.projectsegfau.lt|WWW|v0.31.0|🇱🇺 LU|||
|https://libreddit.bus-hit.me|WWW|v0.31.0|🇨🇦 CA|||
|https://reddit.invak.id|WWW|v0.31.0|🇧🇬 BG|||
|https://redlib.catsarch.com|WWW|v0.31.2|🇺🇸 US|||
|https://reddit.idevicehacked.com|WWW|v0.31.0|🇺🇸 US|||
|https://redlib.freedit.eu|WWW|v0.31.2|🇺🇸 US|||
|https://redlib.perennialte.ch|WWW|v0.31.0|🇦🇺 AU|✅||
|https://redlib.tux.pizza|WWW|v0.31.0|🇺🇸 US|||
|https://redlib.vimmer.dev|WWW|v0.31.2|🇵🇱 PL|||
|https://libreddit.privacydev.net|WWW|v0.31.0|🇫🇷 FR|||
|https://lr.n8pjl.ca|WWW|v0.31.2|🇨🇦 CA|||
|https://reddit.owo.si|WWW|v0.31.0|🇩🇪 DE|||
|https://redlib.ducks.party|WWW|v0.31.0|🇳🇱 NL|||
|https://red.ngn.tf|WWW|v0.31.0|🇹🇷 TR|||
|https://red.artemislena.eu|WWW|v0.31.0|🇩🇪 DE||Be crime do gay|
|https://redlib.dnfetheus.xyz|WWW|v0.31.0|🇧🇷 BR|✅||
|https://redlib.cow.rip|WWW|v0.31.0|🇮🇳 IN|✅||
|https://libreddit.eu.org|WWW|v0.31.0|🇩🇪 DE|||
|https://r.darrennathanael.com|WWW|v0.31.0|🇺🇸 US||contact noc at darrennathanael.com|
|https://redlib.kittywi.re|WWW|v0.31.0|🇫🇷 FR|||
|https://redlib.privacyredirect.com|WWW|v0.31.0|🇫🇮 FI|||
|http://redlib.r4focoma7gu2zdwwcjjad47ysxt634lg73sxmdbkdozanwqslho5ohyd.onion|Tor|v0.31.0|🇩🇪 DE|✅||
|http://redlib.catsarchywsyuss6jdxlypsw5dc7owd5u5tr6bujxb7o6xw2hipqehyd.onion|Tor|v0.31.2|🇺🇸 US|||
|http://libreddit.g4c3eya4clenolymqbpgwz3q3tawoxw56yhzk4vugqrl6dtu3ejvhjid.onion|Tor|v0.31.0|🇫🇷 FR|||
|http://reddit.pk47sgwhncn5cgidm7bofngmh7lc7ukjdpk5bjwfemmyp27ovl25ikyd.onion/|Tor|v0.31.0|🇩🇪 DE|||
|http://red.lpoaj7z2zkajuhgnlltpeqh3zyq7wk2iyeggqaduhgxhyajtdt2j7wad.onion|Tor|v0.31.0|🇩🇪 DE||Onion of red.artemislena.eu|
For information on instance uptime, see the [Uptime Robot status page](https://stats.uptimerobot.com/mpmqAs1G2Q).
# Comparison
This section outlines how Redlib compares to Reddit in terms of speed and privacy.
## Speed
Last tested on January 12, 2024.
Results from Google PageSpeed Insights ([Redlib Report](https://pagespeed.web.dev/report?url=https%3A%2F%2Fredlib.matthew.science%2F), [Reddit Report](https://pagespeed.web.dev/report?url=https://www.reddit.com)).
| Performance metric | Redlib | Reddit |
| ------------------- | -------- | --------- |
| Speed Index | 0.6s | 1.9s |
| Performance Score | 100% | 64% |
| Time to Interactive | **2.8s** | **12.4s** |
## Privacy
### Reddit
**Logging:** According to Reddit's [privacy policy](https://www.redditinc.com/policies/privacy-policy), they "may [automatically] log information" including:
- IP address
- User-agent string
- Browser type
- Operating system
- Referral URLs
- Device information (e.g., device IDs)
- Device settings
- Pages visited
- Links clicked
- The requested URL
- Search terms
**Location:** The same privacy policy goes on to describe that location data may be collected through the use of:
- GPS (consensual)
- Bluetooth (consensual)
- Content associated with a location (consensual)
- Your IP Address
**Cookies:** Reddit's [cookie notice](https://www.redditinc.com/policies/cookies) documents the array of cookies used by Reddit including/regarding:
- Authentication
- Functionality
- Analytics and Performance
- Advertising
- Third-Party Cookies
- Third-Party Site
### Redlib
#### Server
- **Logging:** In production (when running the binary, hosting with docker, or using the official instances), Redlib logs nothing. When debugging (running from source without `--release`), Redlib logs post IDs fetched to aid with troubleshooting.
- **Cookies:** Redlib uses optional cookies to store any configured settings in [the settings menu](https://safereddit.com//settings). These are not cross-site cookies and the cookies hold no personal data.
*Settings and subscriptions are saved in browser cookies. Clearing your cookies will reset them. You can restore your current settings and subscriptions after clearing your cookies using the link given in the settings menu.*
[TIP]
🔗 Want to automatically redirect Reddit links to Redlib? Use [LibRedirect](https://github.com/libredirect/libredirect) or [Privacy Redirect](https://github.com/SimonBrazell/privacy-redirect)!
**Note: The above text presents an abridged and modified version of information found in the [developer's documentation](https://github.com/redlib-org/redlib?tab=readme-ov-file#table-of-contents). Some context has been removed or altered for brevity. For the full and unmodified documentation, please see the [original source](https://github.com/redlib-org/redlib).**
### Additional Information on Frontends from [Privacy Guides](https://www.privacyguides.org/en/frontends/)
>Sometimes services will try to force you to sign up for an account by blocking access to content with annoying popups. They might also break without JavaScript enabled. Frontends can allow you to get around these restrictions.
>If you choose to self-host these frontends, it is important that you have other people using your instance as well in order for you to blend in. You should be careful with where and how you are hosting, as other peoples' usage will be linked to your hosting.
>When you are using an instance run by someone else, make sure to read the privacy policy of that specific instance. They can be modified by their owners and therefore may not reflect the default policy. Some instances have Tor .onion addresses which may grant some privacy as long as your search queries don't contain PII.
### Screenshots:








Breezy Weather is a free and open-source Android weather app, forked from Geometric Weather, adding new features, sources, modernizing code, fixing bugs, updating dependencies for security reasons, etc., while keep having a smooth user and developer experience in mind.
### [Features](https://github.com/breezy-weather/breezy-weather#features)
- Weather data
- Daily and hourly forecasts up to 16 days
- Temperature
- Air quality
- Wind
- UV index
- Precipitation
- Feels like temperature
- Hourly forecasts
- Humidity / Dew point
- Pressure
- Cloud cover
- Visibility
- Precipitation in the next hour
- Air quality
- Pollen & Mold
- Ephemeris (Sun & Moon)
- Severe weather and precipitation alerts
- Real-time weather conditions
- Temperature
- Feels like
- Wind
- UV index
- Humidity
- Dew point
- Atmospheric pressure
- Visibility
- Cloud cover
- Ceiling
- Multiple weather sources
- Large selection of home screen widgets for at-a-glance information
- Live wallpaper
- Custom icon packs
- Geometric Weather icon packs
- Chronus Weather icon packs
- Automatic dark mode
- Looking for radar? Check out this document
- Free and Open Source
- No proprietary blobs/dependencies (versions 5.0.0-alpha and later)
- Releases generated by GitHub actions, guaranteeing it matches the source code
- Fully works with Open-Meteo (FOSS source)
- Privacy-friendly
- No personal data collected by the app (link to app privacy policy)
- Multiple sources are available, with links to their privacy policies for transparency
- Current location is optional and not added by default
- If using current location, an IP location service can be used instead of GPS to send less accurate coordinates to weather source
- No trackers/automatic crash reporters
*Note: If the link isn’t working for you or if you can’t find the app, update the default F-Droid repository in your F-Droid client.*
>The EU Court ruled that “Backdoors may also be exploited by criminal networks and would seriously compromise the security of all users’ electronic communications. The Court takes note of the dangers of restricting encryption described by many experts in the field.” Any requirement to build in backdoors to encryption protocols for law enforcement agencies could also be taken advantage of by malicious actors.
>The EU Court of Human Rights’ also builds on their acknowledgment that “mass surveillance does not appear to have contributed to the prevention of terrorist attacks, contrary to earlier assertions made by senior intelligence officials.”
>As the EU Commision’s Chat Control Bill directly targets undermining secure end-to-end encryption, it now looks to be in trouble. In its current version, the Chat Control bill would require the scanning of content on your personal devices, including that which is sent via end-to-end encrypted messenger apps or encrypted email. At some point, providers would be required to either break this encryption to allow the scanning of content or scan content once it has been decrypted and is readable.
>On February 13th, Europe received an early Valentine’s gift from the European Court of Human rights when they banned any laws that aims to weaken end-to-end encryption. This ruling is a major stumbling block for the EU Chat Control Bill, but does it really mean that Chat Control is dead? There are many reasons why Chat Control should never become law, we've collected the turn of events and steps you can take to help prevent this dangerous bill from ever being passed!
Proton’s Free plan now offers up to 5 GB (up from 1 GB) on Proton Drive and 1 GB (up from 500 MB) on
Announcement from the Proton team on [Reddit](https://www.reddit.com/r/ProtonDrive/comments/1avicc5/the_free_proton_drive_plan_is_getting_5x_the/) ([Libreddit link](https://farside.link/libreddit/r/ProtonDrive/comments/1avicc5/the_free_proton_drive_plan_is_getting_5x_the/)):
>Today, we’re increasing file storage limits on the free plan.
>
>Instead of sharing 1 GB between files and email, you’ll now have:
>
> 5 GB for Proton Drive
>
> 1 GB for Proton Mail
Additional context: For Proton Drive, you now start with 2 GB and for Proton Mail, you start with 500 MB. After signing up for the Free plan, you can unlock the maximum storage allowance on each service thus:
You can boost your Proton Mail storage from 500 MB to 1 GB by completing four [account setup actions](https://proton.me/support/get-started-mail).
You can boost your Proton Drive storage from the default 2 GB to 5 GB by completing three [tasks](https://proton.me/support/more-storage-proton-drive).
*deleted by creator*
About Platform Tilt:
This [dashboard](https://mozilla.github.io/platform-tilt/) tracks technical issues in major software platforms which disadvantage Firefox relative to the first-party browser. We consider aspects like security, stability, performance, and functionality, and propose changes to create a more level playing field.
Further discussion on the live issues can be found in our [platform-tilt issue tracker. ](https://github.com/mozilla/platform-tilt/)
Mozilla's blog [post](https://blog.mozilla.org/netpolicy/2024/01/19/platform-tilt/):
Browsers are the principal gateway connecting people to the open Internet, acting as their agent and shaping their experience. The central role of browsers has long motivated us to build and improve Firefox in order to offer people an independent choice. However, this centrality also creates a strong incentive for dominant players to control the browser that people use. The right way to win users is to build a better product, but shortcuts can be irresistible — and there’s a long history of companies leveraging their control of devices and operating systems to tilt the playing field in favor of their own browser.
*This tilt manifests in a variety of ways. For example: making it harder for a user to download and use a different browser, ignoring or resetting a user’s default browser preference, restricting capabilities to the first-party browser, or requiring the use of the first-party browser engine for third-party browsers.*
For years, Mozilla has engaged in dialog with platform vendors in an effort to address these issues. With renewed public attention and an evolving regulatory environment, we think it’s time to publish these concerns using the same transparent process and tools we use to develop positions on emerging technical standards. So today we’re publishing a new issue tracker where we intend to document the ways in which platforms put Firefox at a disadvantage and engage with the vendors of those platforms to resolve them.
This tracker captures the issues we experience developing Firefox, but we believe in an even playing field for everyone, not just us. We encourage other browser vendors to publish their concerns in a similar fashion, and welcome the engagement and contributions of other non-browser groups interested in these issues. We’re particularly appreciative of the efforts of Open Web Advocacy in articulating the case for a level playing field and for documenting self-preferencing.
People deserve choice, and choice requires the existence of viable alternatives. Alternatives and competition are good for everyone, but they can only flourish if the playing field is fair. It’s not today, but it’s also not hard to fix if the platform vendors wish to do so.
We call on Apple, Google, and Microsoft to engage with us in this new forum to speedily resolve these concerns.















deleted by creator